Difference between revisions of "OPS235 Lab 7 - CentOS7"
| Line 191: | Line 191: | ||
[[Image:Tunnel.png|thumb|right|600px|You can also use an ssh connection to '''tunnel other types of traffic'''. There could be different reasons for doing this. For example tunneling traffic for an unencrypted application/protocol through ssh can '''increase the security of that application''' (i.e. deceive potential hackers).<br><br>Alternatively you could use it to '''circumvent a firewall that is blocking traffic''' you wish to use but allows ssh traffic to pass through.]] | [[Image:Tunnel.png|thumb|right|600px|You can also use an ssh connection to '''tunnel other types of traffic'''. There could be different reasons for doing this. For example tunneling traffic for an unencrypted application/protocol through ssh can '''increase the security of that application''' (i.e. deceive potential hackers).<br><br>Alternatively you could use it to '''circumvent a firewall that is blocking traffic''' you wish to use but allows ssh traffic to pass through.]] | ||
# For this section, you will still be using your '''centos1''' and '''centos2''' VMs. | # For this section, you will still be using your '''centos1''' and '''centos2''' VMs. | ||
| − | # | + | # We will be bypassing a firewall that blocks http traffic. |
| − | # In this investigation centos1 will be your http server and centos2 will be your client. | + | # In this investigation, '''centos1''' will be your '''http server''' and '''centos2''' will be your <u>client</u>. |
| − | # On the HTTP server make sure the Apache web server is installed by typing the command:<br /><b><code><span style="color:#3366CC;font-size:1.2em;">rpm -q httpd</span></code></b> | + | # On the HTTP server, make sure that the Apache web server is installed by typing the command:<br /><b><code><span style="color:#3366CC;font-size:1.2em;">rpm -q httpd</span></code></b> |
| − | # If it is installed check the configuration of the service to see if it is automatically started at any | + | # If it is installed check the configuration of the service to see if it is automatically started at any run-levels by using the <b>chkconfig h</b> command. |
# If it has not been started automatically start the service using the '''service''' command. | # If it has not been started automatically start the service using the '''service''' command. | ||
# Confirm that httpd is listening to TCP/80 using the '''netstat''' command. | # Confirm that httpd is listening to TCP/80 using the '''netstat''' command. | ||
| Line 206: | Line 206: | ||
# Once the tunnel is established use '''netstat''' to verify the port 20808 is listening on '''centos2''' | # Once the tunnel is established use '''netstat''' to verify the port 20808 is listening on '''centos2''' | ||
# Now using the browser on '''centos2''' connect to '''http://localhost:20808''' | # Now using the browser on '''centos2''' connect to '''http://localhost:20808''' | ||
| − | #You should see the index.html page on centos1. | + | #You should see the '''index.html''' page on '''centos1'''. |
# Close the ssh connection and verify that the port 20808 is no longer listening. | # Close the ssh connection and verify that the port 20808 is no longer listening. | ||
Revision as of 13:08, 25 June 2015
Contents
LAB PREPARATION
Purpose / Objectives of Lab 7
Setting up a computer network is very important, but there are many other operations that occur on a daily basis that can include trouble-shooting and repairing network connection issues and maintaining network security. System administrators need to protect or "harden" their computer networks from "penetration" from unauthorized computer users. Hardening a computer system can range from running an IDS (Intrusion Detection System) to monitoring and flagging suspicious activity to implementing screen savers on workstations.
In this lab, you will learn how to use ssh, scp, sftp commands to securely access and share data between authorized personnel. In addition, you will learn various methods of running and configuring an ssh server which include: using Public Key Authentication, settings up an SSH tunnel in order to securely run graphical applications safely among computers in the network, disabling root login, and changing the default ssh communication port to mislead potential penetration testers (also known as "pen-testers" or "hackers").
Main Objectives
- To set up, configure Secure Shell Services (ssh/sshd)
- To use the ssh, scp, and sftp clients to access, copy, or transfer data among Linux servers in a secure manner
- Use ssh to tunnel X applications
- To tunnel network traffic via other communication ports
- To customize sshd to create a more private, secure system
Minimum Required Materials
My Toolkit (CLI Reference)
| Networking Utilities | Additional Utilities: | Configuration Files: |
INVESTIGATION 1: CONFIGURING AND ESTABLISHING AN SSH CONNECTION
Part 1: Enabling the sshd service.
- Use your c7host machine to complete this section
- OpenSSH should have been installed by default. Let's confirm this by issuing the command:
rpm -qa | grep ssh - You should see a number of packages installed including openssh-clients and openssh-server
-
openssh-serverinstalls a service called sshd. Confirm that this service is running by issuing the command:service sshd status - Also, check that the sshd service is configured to start automatically:
chkconfig --list sshd - Now that you know the service is running investigate what port number and protocol sshd uses by issuing the command:
netstat -atunp - What protocol and port is the sshd process using? What is the state of the port? Why wouuld you think that UDP ports don't have a state?
- Reissue the
netstatcommand without the -n option. What is the difference? - How is the file /etc/services related to the difference?
- netstat is a very useful command for anything to do with networking. Read the man pages and make sure you understand the netstat command's output.
- Make sure the sshd service is running on all 3 of your VM's
Answer Part 1 observations / questions in your lab log book.
Part 2: Establishing a Safe SSH Connection: Public Key Authentication
- Use your centos2 VM to complete this section.
- Establish an ssh connection to your centos3 VM using the command:
ssh ops235@centos3
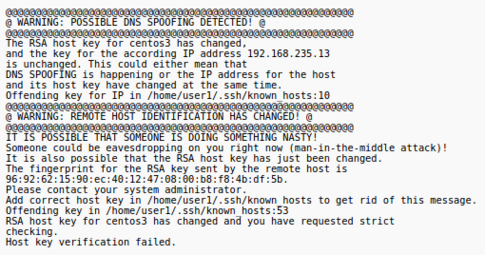
(Where 'ops235' is the account on centos3 and 'centos3' is the hostname of the centos3 VM.) - You should receive a message similar to the following:
- The authenticity of host 'centos3 (192.168.235.13)' can't be established.
- RSA key fingerprint is 53:b4:ad:c8:51:17:99:4b:c9:08:ac:c1:b6:05:71:9b.
- Are you sure you want to continue connecting (yes/no)? yes
- Warning: Permanently added 'centos3' (RSA) to the list of known hosts.
- The authenticity of host 'centos3 (192.168.235.13)' can't be established.
- Answer yes to add to the list of known hosts.
- Logout of your ssh connection by typing
exit. - Run the netstat command in another terminal and check the state of the connection after logging out. Wait a few minutes and then check again. Record your observations.
- Make certain to exit all connections, and that your shell is located in your centos3 server. You can verify this by entering the command:
hostname - Use the Internet to search for "TCP 3 way handshake" to see how TCP connections are established and closed.
- So far, we have learned to establish an ssh connection to another host using a password to establish your identity. But passwords are not the only or even the best way of authenticating your identity. We can also use Public/Private key encryption.
- Public Key authentication is a method of establishing identity using a pair of encryption keys that are designed to work together. One key is known as your private key (which as the name suggests should remain private and protected) and the other is known as the public key (which as the name suggests can be freely distributed) The keys are designed to work together to encrypt data asymmetrically, that is to say that when we encrypt data with one of the keys it can only be decrypted with the other key from the pair.
- While it doesn't mean the message is secure as anybody could decrypt it with the public key, it does establish my identity, if the host can successfully decrypt the message then it must have come from the one person in possession of the private key.
- Start by generating a keypair as your learn account on centos2 using the command:
ssh-keygen - That should generate output similar to the following:
- Generating public/private rsa key pair.
- Enter file in which to save the key (/home/user1/.ssh/id_rsa):
- Enter passphrase (empty for no passphrase):
- Enter same passphrase again:
- Your identification has been saved in /home/user1/.ssh/id_rsa.
- Your public key has been saved in /home/user1/.ssh/id_rsa.pub.
- The key fingerprint is:
- 93:58:20:56:72:d7:bd:14:86:9f:42:aa:82:3d:f8:e5 user1@centos2
- Generating public/private rsa key pair.
- After generating the keys it prompts you for the location to save the keys. The default is ~/.ssh Your private key will be saved as id_rsa and your public key will be saved as id_rsa.pub
- You will then be prompted for a pass-phrase. The pass-phrase must be entered in order to use your private key. Pass-phrases are more secure than passwords and should be lengthy, hard to guess and easy to remember. For example one pass-phrase that meets this criteria might be "seneca students like fish at 4:00am". Avoid famous phrases such as "to be or not to be" as they are easy to guess. It is possible to leave the pass-phrase blank but this is dangerous. It means that if a hacker were able to get into your account they could then use your private key to access other systems you use.
- Now issue the command
ssh-copy-id -i ~/.ssh/id_rsa.pub centos3 - Now we can ssh into centos3 from centos2 using two different authentication methods.
- Make certain to logout of your centos3 system. Use the hostname command to verify you are back in your centos2 server.
Answer Part 2 observations / questions in your lab log book.
INVESTIGATION 2: USING SSH AND OTHER SECURE SHELL UTILITIES
Part 1: How do you use scp and sftp.
- Remain in your centos2 VM for this section.
- To connect to a remote host type the command:
sftp ops235@centos3 - This will establish an interactive session after authentication.
- Type
helpto see the list of sftp commands at any time. - The 2 main commands are
putto copy a file from the local host to the remote host (upload) andgetto copy a file from the remote host to the local host (download). - Try using sftp to transfer files back and forth between hosts.
- You can also use the scp command to copy files to and from remote hosts and even from one remote host to another.
- Use scp to copy your services file to the centos3 host into the /tmp directory. (The path on a remote host follows the :) using the command:
scp /etc/services ops235@centos3:/tmp - Experiment with scp to copy a file from centos3 directly to centos1.
Answer Part 1 observations / questions in your lab log book.
Part 2: How do you use ssh to tunnel X.
- You can also use ssh to tunnel window and bitmap information, allowing us to login to a remote desktop host and run a Xwindows application such as gedit or firefox and the application will run on the remote host but be displayed on the local host.
- For this section, you will be using your centos1 and centos2 VMs.
- From centos2 ssh to centos1' using the following command:
ssh -X -C user@centos1(Where 'user' is your learn account on centos1)
(The -X option enables the forwarding of X window information, and the -C option enables compression for better performance). - Once connected run the gedit application. (Gnome Text Editor)
- The gedit window will display on centos2 but it is running centos1.
- Enter some text and save a file with gedit.
- Exit the gedit application.
- Where was the file saved?
- Experiment with running other GUI applications through ssh.
Answer Part 2 observations / questions in your lab log book.
INVESTIGATION 3: SECURING THE SSH CONNECTION
Part 1: How do you use ssh to tunnel other traffic.
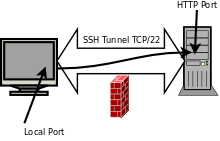
Alternatively you could use it to circumvent a firewall that is blocking traffic you wish to use but allows ssh traffic to pass through.
- For this section, you will still be using your centos1 and centos2 VMs.
- We will be bypassing a firewall that blocks http traffic.
- In this investigation, centos1 will be your http server and centos2 will be your client.
- On the HTTP server, make sure that the Apache web server is installed by typing the command:
rpm -q httpd - If it is installed check the configuration of the service to see if it is automatically started at any run-levels by using the chkconfig h command.
- If it has not been started automatically start the service using the service command.
- Confirm that httpd is listening to TCP/80 using the netstat command.
- Create a small html document called /var/www/html/index.html that displays a short message.*
- On the centos1 (the http server) confirm everything is working locally by using a browser to connect to http://localhost
- Set the default firewall configuration on centos1 to REJECT incoming requests to http (TCP/80)
- Confirm that you can't connect by using firefox on centos to connect to centos1 http://centos1/
- On centos2 confirm that the httpd service is stopped so it cannot interfere with your observations.
- The next step is to establish a tunnel. When you establish a tunnel you make an ssh connection to a remote host and open a new port on the local host. That local host port is then connected to a port on the remote host through the established tunnel. When you send requests to the local port it is forwarded through the tunnel to the remote port.
- Establish a tunnel using a local port on centos2 of 20808, that connects to the remote port on centos1 of 80, using the following command on centos2:
ssh -L 20808:centos1:80 user@centos1
Note:
The -L option (which means Local port) takes one argument:
<local-port>:<connect-to-host>:<connect-to-port>
The command basically connects your local port of 20808 to the remote port of 80 on centos1.
This means all requests to 20808 on the localhost (centos2) are actually tunnelled through your ssh connection
to port 22 on centos1 and then delivered to port 80 on centos1, bypassing the firewall. - Once the tunnel is established use netstat to verify the port 20808 is listening on centos2
- Now using the browser on centos2 connect to http://localhost:20808
- You should see the index.html page on centos1.
- Close the ssh connection and verify that the port 20808 is no longer listening.
Answer Part 1 observations / questions in your lab log book.
Part 2: Making sshd More Secure
- For this section, you will still be using your centos1 and centos2 VMs.
- Think of a good quality password and change your root passwords on all 3 VM's to be more secure. (It would be a good idea to do this for non-root accounts also)
- The next change you can make is to prevent the root account from logging in to sshd altogether.
- Edit the file /etc/ssh/sshd_config and look for the option >PermitRootLogin. Uncomment the option (or add the option if it does not appear) and change the option value to "no".
- Even better, it is possible to restrict access to just specific users that require it.
- Edit the file /etc/ssh/sshd_config and add a new option of "AllowUsers account" using your login account for account.
- In order for these changes to be effective, issue the following command to restart the sshd service:
service sshd restart - Now any hacking attempt also has to guess an account name as well as the password. If you need to ssh with root access, ssh as a regular user and use su - to become root.
- Next change the default port number that sshd uses (TCP:22).
- Edit the sshd configuration file again and change the port number it uses to 2200.
- Restart the service.
- Confirm the new port is being used with the netstat command.
- Before we can use this new port we must change our firewall to allow traffic through the new port number and block access to port 22 by issuing the command:
iptables -I INPUT -p tcp -s0/0 --dport 2200 -j ACCEPTiptables -I INPUT -p tcp -s0/0 --dport 22 -j DROP - To test the new port connect to centos1 from centos2 using the following command:
ssh -p 2200 user@centos1
- Finally as a system administrator you should periodically monitor your system logs for unauthorized login attempts.
- On CentOS systems the log file that is used is /var/log/secure
- It also logs all uses of the su and sudo commands.
- Attempt to connect to all of your VM's as root and other users using both public key and password authentication. Use some su and sudo commands also.
- Inspect the log to see what kind of information is logged.
Answer Part 2 observations / questions in your lab log book.
LAB 7 SIGN-OFF (SHOW INSTRUCTOR)
Arrange proof of the following on the screen:
- ✓ centos2 VM:
- have tunneled Xwindows application from centos1 via ssh
- have tunneled http through firewall using ssh (on web-browser
- have secured ssh against root access
- ✓ centos3 VM:
- have configured sshd to allow connection to centos3 VM
- have logged in centos3 VM using public key authentication
- have scp'd and sftp'd files to centos3 VM
- ✓ c7host Machine:
- Confirmation that sshd is running on host machine
- ✓ Lab7 log-book filled out.
Preparing for Quizzes
- What port does sshd use by defaults?
- What file is used to configure sshd?
- What sftp commands are used to upload/download files?
- What kind of files are stored in the "~/.ssh/" directory?
- How do you determine whether the sshd service is running on your system or not?
- What is the purpose of the ~/.ssh/known_hosts file?
- What is the purpose of the ~/.ssh/authorized_keys file?
- Which system log file records each use of the sudo command?
- How do you stop the sshd service?
- How do you tunnel XWindows applications?
- What port is the default scp port?
- What port(s) is/are used by httpd service?