Difference between revisions of "GPU610/DPS915 MCM Decrypt"
(→Assignment 2) |
(→Kernel Attempts) |
||
| Line 45: | Line 45: | ||
So far I have made attempts to convert different pieces of compute heavy code into kernels in order to obtain the same results as the original code but none have been successful. | So far I have made attempts to convert different pieces of compute heavy code into kernels in order to obtain the same results as the original code but none have been successful. | ||
| + | Original Code 1: | ||
| + | <source lang="cpp"> | ||
| + | unsigned long nr=1345345333L; | ||
| + | unsigned long add=7; | ||
| + | unsigned long nr2=0x12345671L; | ||
| + | unsigned long tmp; | ||
| + | int passLen = strlen(password); | ||
| + | |||
| + | for (int i = 0; i < passLen; i++) { | ||
| + | if (*password == ' ' || *password == '\t') | ||
| + | continue; | ||
| + | tmp= (unsigned long) (unsigned char) password[i]; | ||
| + | nr^= (((nr & 63)+add)*tmp)+ (nr << 8); | ||
| + | nr2+=(nr2 << 8) ^ nr; | ||
| + | add+=tmp; | ||
| + | } | ||
| + | </source> | ||
| + | |||
| + | Kernel Attempt 1: | ||
| + | <source lang="cpp"> | ||
| + | __global__ void hash_password_kernel(unsigned long* nr, unsigned long* nr2, unsigned long* add, const char *password) { | ||
| + | int idx = blockIdx.x * blockDim.x + threadIdx.x; | ||
| + | |||
| + | unsigned long tmp; | ||
| + | |||
| + | tmp= (unsigned long) (unsigned char) password[threadIdx.x]; | ||
| + | *nr^= (((*nr & 63)+*add)*tmp)+ (*nr << 8); | ||
| + | *nr2+=(*nr2 << 8) ^ *nr; | ||
| + | *add+=tmp; | ||
| + | |||
| + | } | ||
| + | </source> | ||
| + | |||
| + | Original Code 2: | ||
| + | <source lang="cpp">for(int i=pos; i<max; i++) { | ||
| + | if(data[i] != max) { | ||
| + | data[i]++; | ||
| + | pos=i; | ||
| + | break; | ||
| + | } | ||
| + | } | ||
| + | |||
| + | </source> | ||
| + | |||
| + | Kernel Attempt 2: | ||
<source lang="cpp"> | <source lang="cpp"> | ||
__global__ void testKernel(unsigned char *data, unsigned int max, unsigned int* pos) { | __global__ void testKernel(unsigned char *data, unsigned int max, unsigned int* pos) { | ||
| − | if(data[threadIdx.x] != max) { | + | if(data[threadIdx.x] != max) { |
| − | data[threadIdx.x]++; | + | data[threadIdx.x]++; |
| − | *pos=threadIdx.x; | + | *pos=threadIdx.x; |
| − | + | } | |
| − | } | ||
} | } | ||
Revision as of 18:24, 1 November 2013
Contents
MySQL Decrypt
Team Members
Progress
Assignment 1
Topic
I have always been interested in computer security, and especially interested in the algorithms used encrypt the passwords that are stored in various databases. After browsing around multiple open source code repositories I found a relatively simplistic C program (which I am planning on converting to C++ at a later date) that is used to decrypt MYSQL passwords given the MYSQL hash of the password.
Required Files
https://drive.google.com/#folders/0B63ZcmSNsUsqX3MyTGNSeFBuSlU
Compilation And Running
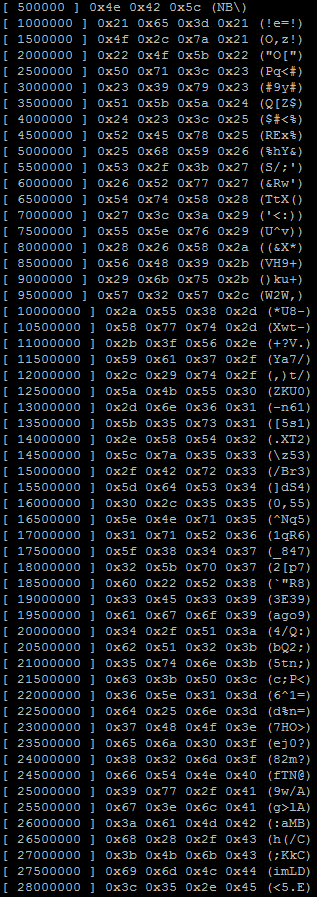
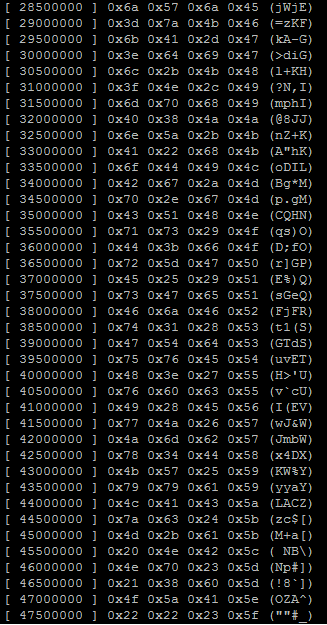
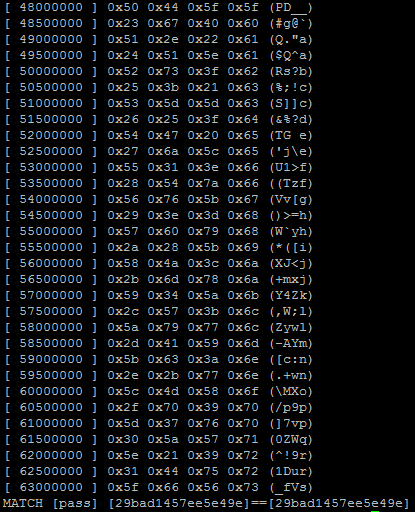
Below you will see a compilation and example run of the application with the hash 29bad1457ee5e49e (which
equals the password pass (a small password so I could test the application in a short period of time).
![]()
Output
Profile
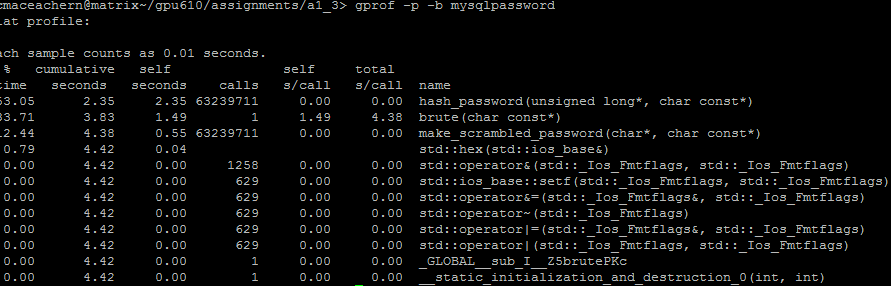
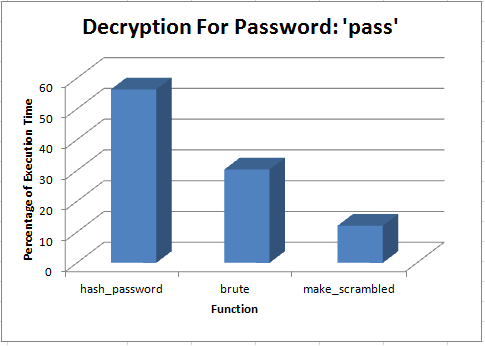
After looking at the code and profiling it, I believe that there are multiple areas which could be parallelized and optimised to reduce the execution time significantly. Most of the execution time takes place in the brute(char const*) and hash_password(unsigned long*, char const*) functions, so I will focus most of my effort and time into those areas when the time comes to optimise them.
Assignment 2
Kernel Attempts
So far I have made attempts to convert different pieces of compute heavy code into kernels in order to obtain the same results as the original code but none have been successful.
Original Code 1:
unsigned long nr=1345345333L;
unsigned long add=7;
unsigned long nr2=0x12345671L;
unsigned long tmp;
int passLen = strlen(password);
for (int i = 0; i < passLen; i++) {
if (*password == ' ' || *password == '\t')
continue;
tmp= (unsigned long) (unsigned char) password[i];
nr^= (((nr & 63)+add)*tmp)+ (nr << 8);
nr2+=(nr2 << 8) ^ nr;
add+=tmp;
}Kernel Attempt 1:
__global__ void hash_password_kernel(unsigned long* nr, unsigned long* nr2, unsigned long* add, const char *password) {
int idx = blockIdx.x * blockDim.x + threadIdx.x;
unsigned long tmp;
tmp= (unsigned long) (unsigned char) password[threadIdx.x];
*nr^= (((*nr & 63)+*add)*tmp)+ (*nr << 8);
*nr2+=(*nr2 << 8) ^ *nr;
*add+=tmp;
}Original Code 2:
for(int i=pos; i<max; i++) {
if(data[i] != max) {
data[i]++;
pos=i;
break;
}
}Kernel Attempt 2:
__global__ void testKernel(unsigned char *data, unsigned int max, unsigned int* pos) {
if(data[threadIdx.x] != max) {
data[threadIdx.x]++;
*pos=threadIdx.x;
}
}