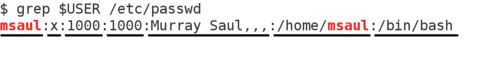Difference between revisions of "OPS235 Lab 4"
(→INVESTIGATION 3: CREATING LINUX COMMANDS VIA SHELL SCRIPTS) |
|||
| (42 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
| − | |||
| − | |||
=LAB PREPARATION= | =LAB PREPARATION= | ||
{| width="40%" align="right" cellpadding="10" | {| width="40%" align="right" cellpadding="10" | ||
| Line 13: | Line 11: | ||
There are many other tasks that a Linux system administrator must perform other than installing Linux and installing software. | There are many other tasks that a Linux system administrator must perform other than installing Linux and installing software. | ||
| − | + | User account management is a very important operation that a Linux sysadmin does on an continual basis. The sysadmin not only needs to add or remove user accounts by issuing commands, but may need to automate user account creations a large number (batch) of potential employees. There are many features with the Linux command to create new users including: specification of a home directory, type of shell used, name, password and time-limit (referred to as "aging") for a new user account. Removing user accounts also have options such as removing the user account but keeping the home directory for reference or evidence of "wrong-doing" | |
| + | |||
| + | Another important operation for a Linux sysadmin is to manage services (eg. starting, restarting, stopping, disabling, enabling system services). | ||
| + | Many students may think that the following topic is small and "not a big deal". Those students may say, '''"How hard is running and stopping services?"''' | ||
| + | The process may not be hard, but knowing how to stop, start, restart and check the status of services is absolutely critical to a Linux server. '''Aside from learning to trouble-shoot problems''' by checking the status of running services, '''understanding how to manage services is critical to help protect a Linux server from penetration''' (this term is referred to as "'''Hardening a system'''"). Sometimes it is "what we don't know" that can harm us. One key element in hardening a computer system is to disable non essential networkng services to allow IDSs ('''Intrusion Detection Systems''') to focus on a narrower range of policy violations. A Debian-based penetration testing distribution called '''Kali''' (formerly referred to as '''"BackTrax"''') allows sysadmins and security professionals to identify vulnerabilities in their computer systems, and thus improve (harden) their systems against penetration. Learning to monitor the status, enable and disable networking services underlies the '''Backtrax''' motto: '''''"The quieter you are, then more you will hear..."'''''<br><br> | ||
<u>Main Objectives</u>: | <u>Main Objectives</u>: | ||
| Line 24: | Line 26: | ||
:* '''Enabled and Disable services''' on a Linux system. | :* '''Enabled and Disable services''' on a Linux system. | ||
:* Display the '''status of running services''' on a Linux system. | :* Display the '''status of running services''' on a Linux system. | ||
| + | :* Create a Bash shell script to '''generate multiple user accounts''' from a text user database file | ||
| + | |||
{|width="80%" cellspacing="0" | {|width="80%" cellspacing="0" | ||
| Line 42: | Line 46: | ||
|style="padding-left:20px;" |User Management | |style="padding-left:20px;" |User Management | ||
| − | [ | + | [https://www.systutorials.com/docs/linux/man/8-useradd/ useradd]<br> |
| − | [ | + | [https://www.systutorials.com/docs/linux/man/8-userdel/ userdel]<br> |
| − | [ | + | [https://www.systutorials.com/docs/linux/man/8-usermod/ usermod]<br> |
| − | [ | + | [https://www.systutorials.com/docs/linux/man/8-groupadd/ groupadd]<br> |
| − | [ | + | [https://www.systutorials.com/docs/linux/man/8-groupdel/ groupdel]<br> |
[http://www.agr.unideb.hu/~agocs/informatics/11_e_unix/unixhelp/unixhelp.ed.ac.uk/CGI/man-cgied74.html?chage chage]<br><br> | [http://www.agr.unideb.hu/~agocs/informatics/11_e_unix/unixhelp/unixhelp.ed.ac.uk/CGI/man-cgied74.html?chage chage]<br><br> | ||
Managing Services<br> | Managing Services<br> | ||
| − | |||
| − | |||
[http://www.dsm.fordham.edu/cgi-bin/man-cgi.pl?topic=systemctl systemctl]<br> | [http://www.dsm.fordham.edu/cgi-bin/man-cgi.pl?topic=systemctl systemctl]<br> | ||
|style="padding-left:20px;" |Miscellaneous | |style="padding-left:20px;" |Miscellaneous | ||
| Line 59: | Line 61: | ||
[http://zenit.senecac.on.ca/wiki/index.php/Init_vs_systemd init vs systemd] | [http://zenit.senecac.on.ca/wiki/index.php/Init_vs_systemd init vs systemd] | ||
|} | |} | ||
| − | |||
= INVESTIGATION 1: User/Group Management = | = INVESTIGATION 1: User/Group Management = | ||
| − | + | In your ULI101 course, you learned to change permissions for directories and files relating to user, same group members and other group members. In this course, since you are the sysadmin with root privileges, you can create or remove users and groups as well as change the ownership of directories and files! We will now learn to perform key user account management operations in this section. | |
| − | |||
| − | In your ULI101 course, you learned to change permissions for directories and files relating to user, same group members and other group members. In this course, since you are the sysadmin with root privileges, you can create or remove groups as well as change the ownership of directories and files! We will now learn to perform key user account management operations in this section. | ||
| Line 81: | Line 80: | ||
# Launch your '''c7host''' and '''centos1''' VMs. | # Launch your '''c7host''' and '''centos1''' VMs. | ||
| + | # Switch to your '''centos1''' VM. | ||
# Open a shell terminal and login as '''root'''. | # Open a shell terminal and login as '''root'''. | ||
# Look at the <b><code><span style="color:#3366CC;font-size:1.2em;">/etc/passwd</span></code></b> file. | # Look at the <b><code><span style="color:#3366CC;font-size:1.2em;">/etc/passwd</span></code></b> file. | ||
| Line 105: | Line 105: | ||
# Remain in your '''centos1''' VM for this section. | # Remain in your '''centos1''' VM for this section. | ||
# Read the man page for the <b><code><span style="color:#3366CC;font-size:1.2em;">useradd</span></code></b> command. | # Read the man page for the <b><code><span style="color:#3366CC;font-size:1.2em;">useradd</span></code></b> command. | ||
| − | # Create a new user called '''ops235_1''' by issuing the command: | + | # Create a new user called '''ops235_1''' by issuing the command:<br><b><code><span style="color:#3366CC;font-size:1.2em;">useradd ops235_1</span></code></b> |
# Issue the command: <b><code><span style="color:#3366CC;font-size:1.2em;">grep ops235_1 /etc/passwd</span></code></b> to see if that user account was created. | # Issue the command: <b><code><span style="color:#3366CC;font-size:1.2em;">grep ops235_1 /etc/passwd</span></code></b> to see if that user account was created. | ||
| − | # View the '''/home''' directory to view the contents. Is the user ops235_1's home directory there?<br>'''NOTE:''' In some versions of Linux, you may have to issue the -m option with the useradd command in order to create a home directory for that user.<br><br> | + | # View the '''/home''' directory to view the contents. Is the user ops235_1's home directory there?<br><br>'''NOTE:''' In some versions of Linux, you may have to issue the '''-m''' option with the useradd command in order to create a home directory for that user.<br><br> |
| − | # Issue the following command to create the user called ops235_2: | + | # Issue the following command to create the user called ops235_2:<br><b><code><span style="color:#3366CC;font-size:1.2em;">useradd -m ops235_2</span></code></b> |
# View the '''/home''' directory to verify that the home directory for '''ops235_2''' has been created. What does the -m option do for the useradd command? | # View the '''/home''' directory to verify that the home directory for '''ops235_2''' has been created. What does the -m option do for the useradd command? | ||
# Issue the following command to remove the user called ops235_2: <b><code><span style="color:#3366CC;font-size:1.2em;">userdel ops235_2</span></code></b> | # Issue the following command to remove the user called ops235_2: <b><code><span style="color:#3366CC;font-size:1.2em;">userdel ops235_2</span></code></b> | ||
# Issue the grep command with the /etc/passwd file to verify that the username ops235_2 was removed. | # Issue the grep command with the /etc/passwd file to verify that the username ops235_2 was removed. | ||
# View the contents of the '''/home''' directory. Was the home directory for user '''ops235_2''' removed? | # View the contents of the '''/home''' directory. Was the home directory for user '''ops235_2''' removed? | ||
| + | # Issue the following command to remove ops235_2's home directory: <b><code><span style="color:#3366CC;font-size:1.2em;">rm -rf /home/ops235_2</span></code></b> | ||
# Issue the '''userdel''' comamnd to remove the '''ops235_1''' account with the '''-r option''' (and home directory regardless if it exists or not). | # Issue the '''userdel''' comamnd to remove the '''ops235_1''' account with the '''-r option''' (and home directory regardless if it exists or not). | ||
# Issue the useradd -m command to recreate the user called: '''ops235_1'''. | # Issue the useradd -m command to recreate the user called: '''ops235_1'''. | ||
# Use the '''passwd''' command to set the password for the user '''ops235_1'''. | # Use the '''passwd''' command to set the password for the user '''ops235_1'''. | ||
# View the <u>contents</u> for '''ops235_1's''' home directory and note the files. | # View the <u>contents</u> for '''ops235_1's''' home directory and note the files. | ||
| − | # | + | # Create a new file in the '''/etc/skel''' directory with the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">touch /etc/skel/foo</span></code></b> |
| − | |||
# Recreate the new user (with home directories automatically created) for '''ops235_2'''. | # Recreate the new user (with home directories automatically created) for '''ops235_2'''. | ||
# Set the password for the user '''ops235_2'''. | # Set the password for the user '''ops235_2'''. | ||
| Line 124: | Line 124: | ||
# Be sure to record your observations in your lab notes. | # Be sure to record your observations in your lab notes. | ||
#Issue the man pages for the '''useradd''' command. Explain the purpose of using the '''-e''' option for the ''useradd'' command. | #Issue the man pages for the '''useradd''' command. Explain the purpose of using the '''-e''' option for the ''useradd'' command. | ||
| − | #Issue the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">chage -E | + | #Issue the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">chage -E 2019-12-31 ops235_1</span></code></b> |
| − | #Issue the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">usermod -c "New Name" ops235_2</span></code></b>. View ops235_2's account information in the '''/etc/passwd''' file. What do you notice is different? | + | #Issue the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">usermod -c "New Name" ops235_2</span></code></b>. |
| − | # Issue the following command to obtain information regarding the user called ops235_1: <b><code><span style="color:#3366CC;font-size:1.2em;">chage -l ops235_1</span></code></b>. What do you think is the purpose of the chage command and the useradd command with the -e option? | + | #View ops235_2's account information in the '''/etc/passwd''' file. What do you notice is different? |
| + | # Issue the following command to obtain information regarding the user called ops235_1: <b><code><span style="color:#3366CC;font-size:1.2em;">chage -l ops235_1</span></code></b>. What do you think is the purpose of the chage command and the useradd command with the '''-e''' option? | ||
| Line 135: | Line 136: | ||
|} | |} | ||
| + | |||
=== Part 3: Managing Groups === | === Part 3: Managing Groups === | ||
| − | In this section, we will learn how to create, remove and modify groups in our Linux VM. You learned in ULI101 how to change permissions with the '''chmod''' command, but you didn't have admin privileges to create groups to allow directory and regular file sharing. Since you now have admin privileges with your VM, you can now create groups, and add users to this group to allow file-sharing among users. | + | In this section, we will learn how to create, remove and modify groups in our Linux VM. You learned in ULI101 how to change permissions with the '''chmod''' command, but you didn't have admin privileges to '''create groups''' to allow directory and regular file sharing. Since you now have admin privileges with your VM, you can now create groups, and add users to this group to allow file-sharing among users. |
:'''Perform the following steps:''' | :'''Perform the following steps:''' | ||
| − | #Close | + | #Make certain that you are still in your '''centos1''' VM. |
| + | #Close all application windows, and switch user accounts (within your centos1 VM) by clicking on the top right-hand side of the screen (power icon), click '''your regular username''', click '''switch user''', and login as '''"New Name"''' (i.e. ops235_2). | ||
#Open a shell terminal. | #Open a shell terminal. | ||
#Create a file called '''information.txt''' in home directory of that user. | #Create a file called '''information.txt''' in home directory of that user. | ||
| Line 146: | Line 149: | ||
#Issue the command <b><code><span style="color:#3366CC;font-size:1.2em;">su -</span></code></b> to login to your root account. | #Issue the command <b><code><span style="color:#3366CC;font-size:1.2em;">su -</span></code></b> to login to your root account. | ||
#Issue the following command to create a group called '''welcome''': <b><code><span style="color:#3366CC;font-size:1.2em;">groupadd welcome</span></code></b> | #Issue the following command to create a group called '''welcome''': <b><code><span style="color:#3366CC;font-size:1.2em;">groupadd welcome</span></code></b> | ||
| − | #Issue the command: <b><code><span style="color:#3366CC;font-size:1.2em;">grep welcome /etc/group</span></code></b> file to confirm that group was created. | + | #Issue the command: <b><code><span style="color:#3366CC;font-size:1.2em;">grep welcome /etc/group</span></code></b> file to confirm that the group '''welcome''' was created. |
# Read the man page for the <b><code><span style="color:#3366CC;font-size:1.2em;">usermod</span></code></b> command. Which option allow you to set the Group ID number ('''GID''') when you create a new group? Which options allow you to both append and assign users to an existing group name? | # Read the man page for the <b><code><span style="color:#3366CC;font-size:1.2em;">usermod</span></code></b> command. Which option allow you to set the Group ID number ('''GID''') when you create a new group? Which options allow you to both append and assign users to an existing group name? | ||
| − | # Issue | + | # Issue two separate '''usermod''' commands to add both '''ops235_1''' and '''ops235_2''' to the newly-created '''welcome''' group. |
# Verify that both ops235_1 and ops235_2 now belong to the '''welcome''' group. | # Verify that both ops235_1 and ops235_2 now belong to the '''welcome''' group. | ||
| Line 154: | Line 157: | ||
===Practical Example=== | ===Practical Example=== | ||
| − | Management has | + | Management has sent you (the Linux systadmin) that a "new" employee has been hired and will be on on probation for 3 months. As the Linux system administrator, they want you to perform the following steps: |
# Remain in your '''centos1''' VM for this section. | # Remain in your '''centos1''' VM for this section. | ||
| − | # Use the '''useradd''' command to create a user account called: '''noobie''' to expire in 3 months from this date as part of the security policy of this organization. | + | # Use the '''useradd''' command to create a user account called: '''noobie''' to expire in 3 months from this date as part of the security policy of this organization (issue man useradd to determine correct option to set expiry date). |
# Set an appropriate password for this user account. | # Set an appropriate password for this user account. | ||
# Add this newly-created user to the newly-created '''welcome''' group. | # Add this newly-created user to the newly-created '''welcome''' group. | ||
| Line 175: | Line 178: | ||
|} | |} | ||
| − | |||
| − | |||
| − | |||
| − | |||
=== Part 1: How do we Manage System Services? === | === Part 1: How do we Manage System Services? === | ||
| − | + | At the beginning of this lab we mentioned that running unneeded '''packages can be a security risk''' due to the unnecessary increase in the complexity of your system. Similarly, it is also unnecessarily hazardous, and even more so, to leave unneeded services running. In this investigation, we will learn how to '''control services, and turn off those services that we think are not necessary to help reduce security risks'''. | |
Although there is a command called: '''service''' that may appear to manager services on your Linux system, it is considered <u>'''deprecated'''</u> (i.e. "obsolete"). It has been replaced by using the [http://zenit.senecac.on.ca/wiki/index.php/Init_vs_systemd#systemd_Command_Usage systemctl] command. | Although there is a command called: '''service''' that may appear to manager services on your Linux system, it is considered <u>'''deprecated'''</u> (i.e. "obsolete"). It has been replaced by using the [http://zenit.senecac.on.ca/wiki/index.php/Init_vs_systemd#systemd_Command_Usage systemctl] command. | ||
| Line 191: | Line 190: | ||
# To verify the status of your iptables service, issue the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">systemctl status iptables</span></code></b> | # To verify the status of your iptables service, issue the following command: <b><code><span style="color:#3366CC;font-size:1.2em;">systemctl status iptables</span></code></b> | ||
# Use the commands you used in Lab2 to '''stop''' and '''disable''' the iptables service. | # Use the commands you used in Lab2 to '''stop''' and '''disable''' the iptables service. | ||
| − | # Issue a command to verify you '''disabled''' and '''stopped''' the iptables service. | + | # Issue a command to verify you '''disabled''' and '''stopped''' the iptables service.<br><br>'''Note:''' There is a major difference between stopping a service and disabling a service: If a service is stopped but enabled, the service will start upon reboot. Therefore to prevent it being started upon boot-up, the service will need to be disabled as well!<br><br> |
| − | # Issue the commands to '''start''' and '''enable''' the iptables service, and '''verify''' that it is <u>started</u> and <u>enabled</u>. | + | # Issue the commands to '''start''' and '''enable''' the iptables service, and '''verify''' that it is <u>started</u> and <u>enabled</u>.<br><br>'''Note:''' If you performed the commands correctly, the iptables service should be running, and will automatically run upon your Linux machine start-up. |
| + | |||
| + | |||
| + | ===Part 2: How do we Manage Runlevels?=== | ||
| + | Running Linux servers in graphical mode can make the server vulnerable to penetration (i.e. a potential break-in to the server from unauthorized intruders). The X-windows framework can be vulnerable to attacks when these servers are connected to the Internet. This is why when you install '''server versions''' of Linux, they work in text-based mode only. Desktop versions of Linux are then installed on workstations (working in graphical mode) that connect to the '''Linux server''' (for security reasons since those servers are closest to the router and the Internet). | ||
| + | The Linux sysadmin can also change the run-level (or state) of a graphical Linux server to run in text-based mode and run the graphical mode by issuing a command when graphic mode is required. The run-level term is now deprecated in Fedora, and will likely be deprecated in RHEL/CentOS at some point as well, but for now this is what the industry is using. | ||
{| width="50%" align="right" cellpadding="10" | {| width="50%" align="right" cellpadding="10" | ||
|- valign="top" | |- valign="top" | ||
| Line 200: | Line 204: | ||
[[Image:grub2_1.png|thumb|right|600px|The purpose of '''Linux servers''' are to run network-based services (i.e. they '''"serve"''' the users that operating in that Linux/Unix system). It is common that these Linux servers are separated (for security purposes) and they are '''run in Command-Line mode only'''. Running these Linux/Unix servers in '''Graphics Mode will make them more vulnerable to penetration from hackers, etc.''' Therefore, it is common that the Linux servers are CLI <u>only</u>, but the Workstations that connect to them within the network are GUI. Therefore, it is important that a Linux/Unix system administrator understand to switch to these different "run-levels". ]] | [[Image:grub2_1.png|thumb|right|600px|The purpose of '''Linux servers''' are to run network-based services (i.e. they '''"serve"''' the users that operating in that Linux/Unix system). It is common that these Linux servers are separated (for security purposes) and they are '''run in Command-Line mode only'''. Running these Linux/Unix servers in '''Graphics Mode will make them more vulnerable to penetration from hackers, etc.''' Therefore, it is common that the Linux servers are CLI <u>only</u>, but the Workstations that connect to them within the network are GUI. Therefore, it is important that a Linux/Unix system administrator understand to switch to these different "run-levels". ]] | ||
|} | |} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
:'''Perform the following steps:''' | :'''Perform the following steps:''' | ||
# Remain in your '''centos1''' VM for this section. | # Remain in your '''centos1''' VM for this section. | ||
| − | # Issue the following Linux command: <b><code><span style="color:#3366CC;font-size:1.2em;">runlevel</span></code></b> | + | # Issue the following Linux command: <b><code><span style="color:#3366CC;font-size:1.2em;">runlevel</span></code></b><br><br>'''Note:''' You should see two separate characters (like N 5). The number on the right is the current run-level 5 (which is graphical mode). The number or character on the left if the previous run level (which is N which means there was no previous run level since it was a "new" install).<br><br> |
# You can use the '''init''' command to change the current run-level. See a list of runlevels [https://www.centos.org/docs/5/html/5.2/Installation_Guide/s2-init-boot-shutdown-rl.html here]. | # You can use the '''init''' command to change the current run-level. See a list of runlevels [https://www.centos.org/docs/5/html/5.2/Installation_Guide/s2-init-boot-shutdown-rl.html here]. | ||
| − | # Issue the '''init''' command to change the current run-level in '''centos1''' to '''3'''. What | + | # Issue the '''init''' command to change the current run-level in '''centos1''' to '''3''' by issuing the following command:<br><b><code><span style="color:#3366CC;font-size:1.2em;">init 3</span></code></b> |
| − | # Issue the following Linux command: <b><code><span style="color:#3366CC;font-size:1.2em;">startx</span></code></b><br>What happens? | + | # What did you notice? |
| − | # Log-off your graphical system. You should return to your shell prompt. | + | # Issue the following Linux command: <b><code><span style="color:#3366CC;font-size:1.2em;">startx</span></code></b><br>What happens? Why would you want to make a graphical Linux system run in text-based mode? |
| − | # Reissue the init command to change the current run-level back to '''5'''<br>Did it work? | + | # Log-off your graphical system. You should return to your CLI shell prompt and change to root user. You should notice at this point that the command '''startx''' did not reset your run-level. |
| + | # Reissue the '''init''' command to change the current run-level back to '''5'''<br>Did it work? | ||
| + | # Issue the runlevel command to verify that the run-level is set to '''5''' (i.e. Graphical). You should notice a '''3 followed by a 5'''. That is to indicate that the '''current''' run-level is 5, but <u>previously</u>, it was set to 3. | ||
'''Answer INVESTIGATION 2 observations / questions in your lab log book.''' | '''Answer INVESTIGATION 2 observations / questions in your lab log book.''' | ||
| − | + | = INVESTIGATION 3: CREATING USERS VIA SHELL SCRIPTS= | |
| − | = INVESTIGATION 3: CREATING | ||
| Line 236: | Line 235: | ||
#Open a shell terminal, and login as root. | #Open a shell terminal, and login as root. | ||
#Change to the '''/root/bin''' directory. | #Change to the '''/root/bin''' directory. | ||
| − | #Download, study, and run the following shell script. Issue the command:<br><b><code><span style=" | + | #Download, study, and run the following shell script. Issue the command:<br><b><code><span style="cursor:default;color:#3366CC;font-size:1.2em;">wget https://ict.senecacollege.ca/~ops235/labs/user-create.bash</span></code></b> |
#Try to understand what these Bash Shell scripts do, and then run the script as root to create just one user called '''test'''. After running the shell script, view the contents of the '''/home''' directory to confirm. | #Try to understand what these Bash Shell scripts do, and then run the script as root to create just one user called '''test'''. After running the shell script, view the contents of the '''/home''' directory to confirm. | ||
| Line 243: | Line 242: | ||
| − | <ol><li value=" | + | <ol><li value="6">Open a Bash shell terminal and login as root.</li><li>Change to the '''/root/bin''' directory.</li><li>Use the wget command to download the input file called user-data.txt by issuing the command:<br><b><code><span style="color:#3366CC;font-size:1.2em;">wget https://ict.senecacollege.ca/~ops235/labs/user-data.txt</span></code></b></li><li>View the contents on the user-data.txt file to confirm there are 3 fields (username, fullname, and e-mail address)which are separated by the colon (:) symbol.</li><li>Use a text editor (such as <b><code><span style="color:#3366CC;font-size:1.2em;">vi</span></code></b> or <b><code><span style="color:#3366CC;font-size:1.2em;">nano</span></code></b>) to create a Bash Shell script called: <b><code><span style="color:#3366CC;font-size:1.2em;">createUsers.bash</span></code></b> in the /root/bin directory.</li><li>Enter the following text content into your text-editing session:</li></ol> |
<code style="color:#3366CC;font-family:courier;font-size:.9em;margin-left:20px;font-weight:bold;"> | <code style="color:#3366CC;font-family:courier;font-size:.9em;margin-left:20px;font-weight:bold;"> | ||
<br> | <br> | ||
| Line 255: | Line 254: | ||
# Date: *** CURRENT DATE ***<br> | # Date: *** CURRENT DATE ***<br> | ||
<br> | <br> | ||
| − | |||
# Make certain user is logged in as root<br> | # Make certain user is logged in as root<br> | ||
if [ $USER != "root" ]<br> | if [ $USER != "root" ]<br> | ||
| Line 270: | Line 268: | ||
</code> | </code> | ||
<br> | <br> | ||
| − | <ol><li value=" | + | <ol><li value="12">Save your editing session, but remain in the text editor.</li><li>The code displayed below uses the getopt function set the input file pathname or check for invalid options or missing option text. Add the following code</li></ol> |
<br> | <br> | ||
<code style="color:#3366CC;font-family:courier;font-size:.9em;font-weight:bold;"> | <code style="color:#3366CC;font-family:courier;font-size:.9em;font-weight:bold;"> | ||
| Line 286: | Line 284: | ||
done<br> | done<br> | ||
</code> | </code> | ||
| − | <ol><li value=" | + | <ol><li value="14">Save your editing session, but remain in the text editor.</li><li>The code displayed below uses logic to exit the script if the input file does not exist. Command substitution is used to store each line of the input file as a positional parameter. There is one subtle problem here: The full names of the users contain spaces which can create havoc when trying to set each line as a separate positional parameter. In this case the sed command is used to convert spaces to plus signs (+), which will be converted back later. Finally, a '''for''' loop is used to create each account ('''useradd''') and mail the user their account information ('''mail'''). Add the following code:</li></ol> |
<br> | <br> | ||
<code style="color:#3366CC;font-family:courier;font-size:.9em;font-weight:bold;"> | <code style="color:#3366CC;font-family:courier;font-size:.9em;font-weight:bold;"> | ||
| Line 317: | Line 315: | ||
<ol> | <ol> | ||
| − | <li value=" | + | <li value="16">Save, set permissions, and then run that shell script for the input text file '''user-data.txt'''. Did it work? Try running the script without an argument - What did it do? </li><li>You have completed lab4. Proceed to Completing The Lab, and follow the instructions for "lab sign-off".</li></ol> |
'''Answer INVESTIGATION 3 observations / questions in your lab log book.''' | '''Answer INVESTIGATION 3 observations / questions in your lab log book.''' | ||
= LAB 4 SIGN-OFF (SHOW INSTRUCTOR) = | = LAB 4 SIGN-OFF (SHOW INSTRUCTOR) = | ||
| + | ===Exclusively for Summer 2020 term, submissions are accepted only online!=== | ||
| + | Follow the submission instructions for lab 4 on Blackboard. | ||
{{Admon/important|Time for a new backup!|If you have successfully completed this lab, make a new backup of your virtual machines as well as your host machine.}} | {{Admon/important|Time for a new backup!|If you have successfully completed this lab, make a new backup of your virtual machines as well as your host machine.}} | ||
| Line 329: | Line 329: | ||
# Switch to your '''c7host''' VM. | # Switch to your '''c7host''' VM. | ||
# Open a shell terminal, '''su -''' into root, and change to the '''/root/bin''' directory. | # Open a shell terminal, '''su -''' into root, and change to the '''/root/bin''' directory. | ||
| − | # Issue the Linux command: <b><code><span style="color:#3366CC;font-size:1.2em;">wget | + | # Issue the Linux command: <b><code><span style="color:#3366CC;font-size:1.2em;">wget https://ict.senecacollege.ca/~ops235/labs/lab4-check.bash</span></code></b> |
# Give the '''lab4-check.bash''' file execute permissions (for the file owner). | # Give the '''lab4-check.bash''' file execute permissions (for the file owner). | ||
# Run the shell script and if any warnings, make fixes and re-run shell script until you receive "congratulations" message. | # Run the shell script and if any warnings, make fixes and re-run shell script until you receive "congratulations" message. | ||
#Arrange proof of the following on the screen:<br><span style="color:green;font-size:1.5em;">✓</span> '''centos1''' VM:<blockquote><ul><li>Demonstrate that this VM 's current run-level is set to '''5'''.</ul></blockquote><span style="color:green;font-size:1.5em;">✓</span>'''c7host''' machine<blockquote><ul><li>Run the '''lab4-check.bash''' script in front of your instructor (must have all <b><code><span style="color:#66cc00;border:thin solid black;font-size:1.2em;"> OK </span></code></b> messages)</li></ul></blockquote><span style="color:green;font-size:1.5em;">✓</span> '''Lab4''' log-book filled out. | #Arrange proof of the following on the screen:<br><span style="color:green;font-size:1.5em;">✓</span> '''centos1''' VM:<blockquote><ul><li>Demonstrate that this VM 's current run-level is set to '''5'''.</ul></blockquote><span style="color:green;font-size:1.5em;">✓</span>'''c7host''' machine<blockquote><ul><li>Run the '''lab4-check.bash''' script in front of your instructor (must have all <b><code><span style="color:#66cc00;border:thin solid black;font-size:1.2em;"> OK </span></code></b> messages)</li></ul></blockquote><span style="color:green;font-size:1.5em;">✓</span> '''Lab4''' log-book filled out. | ||
| − | |||
= Practice For Quizzes, Tests, Midterm & Final Exam = | = Practice For Quizzes, Tests, Midterm & Final Exam = | ||
| Line 357: | Line 356: | ||
[[Category:OPS235]] | [[Category:OPS235]] | ||
[[Category:OPS235 Labs]] | [[Category:OPS235 Labs]] | ||
| + | [[Category:CentOS 7]] | ||
| + | [[Category:SSD2]] | ||
| + | [[Category:Digital Classroom]] | ||
Latest revision as of 00:15, 9 October 2020
Contents
LAB PREPARATION
Purpose / Objectives of Lab 4
There are many other tasks that a Linux system administrator must perform other than installing Linux and installing software.
User account management is a very important operation that a Linux sysadmin does on an continual basis. The sysadmin not only needs to add or remove user accounts by issuing commands, but may need to automate user account creations a large number (batch) of potential employees. There are many features with the Linux command to create new users including: specification of a home directory, type of shell used, name, password and time-limit (referred to as "aging") for a new user account. Removing user accounts also have options such as removing the user account but keeping the home directory for reference or evidence of "wrong-doing"
Another important operation for a Linux sysadmin is to manage services (eg. starting, restarting, stopping, disabling, enabling system services). Many students may think that the following topic is small and "not a big deal". Those students may say, "How hard is running and stopping services?"
The process may not be hard, but knowing how to stop, start, restart and check the status of services is absolutely critical to a Linux server. Aside from learning to trouble-shoot problems by checking the status of running services, understanding how to manage services is critical to help protect a Linux server from penetration (this term is referred to as "Hardening a system"). Sometimes it is "what we don't know" that can harm us. One key element in hardening a computer system is to disable non essential networkng services to allow IDSs (Intrusion Detection Systems) to focus on a narrower range of policy violations. A Debian-based penetration testing distribution called Kali (formerly referred to as "BackTrax") allows sysadmins and security professionals to identify vulnerabilities in their computer systems, and thus improve (harden) their systems against penetration. Learning to monitor the status, enable and disable networking services underlies the Backtrax motto: "The quieter you are, then more you will hear..."
Main Objectives:
- Administer (add, remove, modify) users on a Linux system.
- Save time while adding new users using a template of start-up files.
- Create and manage groups on a Linux system.
- Start, Restart and Stop services on a Linux system.
- Enabled and Disable services on a Linux system.
- Display the status of running services on a Linux system.
- Create a Bash shell script to generate multiple user accounts from a text user database file
| Minimum Required Materials |
Linux Command Reference | ||||
| User Management
useradd |
Miscellaneous
/etc/passwd | ||||
INVESTIGATION 1: User/Group Management
In your ULI101 course, you learned to change permissions for directories and files relating to user, same group members and other group members. In this course, since you are the sysadmin with root privileges, you can create or remove users and groups as well as change the ownership of directories and files! We will now learn to perform key user account management operations in this section.
Part 1: Studying the /etc/passwd file
The /etc/passwd file is a database that stores user accounts (both system and regular users). Since we will be learning to create, modify and remove users on our Linux system, we should study this file in order to understand how those user account management commands will affect this file.
- Perform the following steps:
- Launch your c7host and centos1 VMs.
- Switch to your centos1 VM.
- Open a shell terminal and login as root.
- Look at the
/etc/passwdfile. - Make note of the contents of that file.
- Read about the file: http://man7.org/linux/man-pages/man5/passwd.5.html
- Make sure you know what information each field contains.
- Why do you think there are so many users?
- Look at the names of the users. What do you think these user names represent? Are they people?
- What is the numeric user ID (UID) of the root user?
- The user IDs of real users (people) are different from the user IDs of system accounts. What is the pattern?
Part 2: Adding, Removing, and Modifying Users
In this section, we will now learn how to properly add user accounts, remove user accounts, and modify existing user account information.
- Perform the following steps:
- Remain in your centos1 VM for this section.
- Read the man page for the
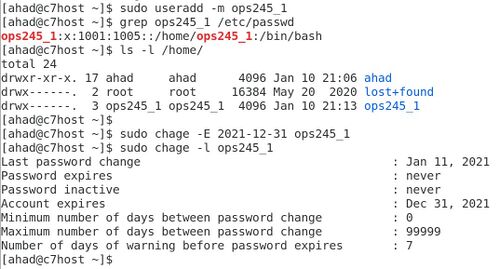
useraddcommand. - Create a new user called ops235_1 by issuing the command:
useradd ops235_1 - Issue the command:
grep ops235_1 /etc/passwdto see if that user account was created. - View the /home directory to view the contents. Is the user ops235_1's home directory there?
NOTE: In some versions of Linux, you may have to issue the -m option with the useradd command in order to create a home directory for that user. - Issue the following command to create the user called ops235_2:
useradd -m ops235_2 - View the /home directory to verify that the home directory for ops235_2 has been created. What does the -m option do for the useradd command?
- Issue the following command to remove the user called ops235_2:
userdel ops235_2 - Issue the grep command with the /etc/passwd file to verify that the username ops235_2 was removed.
- View the contents of the /home directory. Was the home directory for user ops235_2 removed?
- Issue the following command to remove ops235_2's home directory:
rm -rf /home/ops235_2 - Issue the userdel comamnd to remove the ops235_1 account with the -r option (and home directory regardless if it exists or not).
- Issue the useradd -m command to recreate the user called: ops235_1.
- Use the passwd command to set the password for the user ops235_1.
- View the contents for ops235_1's home directory and note the files.
- Create a new file in the /etc/skel directory with the following command:
touch /etc/skel/foo - Recreate the new user (with home directories automatically created) for ops235_2.
- Set the password for the user ops235_2.
- View the contents for ops235_2's home directory and note the files. What do you notice that is different. What do you think is the purpose of the /etc/skel directory?
- Be sure to record your observations in your lab notes.
- Issue the man pages for the useradd command. Explain the purpose of using the -e option for the useradd command.
- Issue the following command:
chage -E 2019-12-31 ops235_1 - Issue the following command:
usermod -c "New Name" ops235_2. - View ops235_2's account information in the /etc/passwd file. What do you notice is different?
- Issue the following command to obtain information regarding the user called ops235_1:
chage -l ops235_1. What do you think is the purpose of the chage command and the useradd command with the -e option?
Part 3: Managing Groups
In this section, we will learn how to create, remove and modify groups in our Linux VM. You learned in ULI101 how to change permissions with the chmod command, but you didn't have admin privileges to create groups to allow directory and regular file sharing. Since you now have admin privileges with your VM, you can now create groups, and add users to this group to allow file-sharing among users.
- Perform the following steps:
- Make certain that you are still in your centos1 VM.
- Close all application windows, and switch user accounts (within your centos1 VM) by clicking on the top right-hand side of the screen (power icon), click your regular username, click switch user, and login as "New Name" (i.e. ops235_2).
- Open a shell terminal.
- Create a file called information.txt in home directory of that user.
- Issue the following command:
ls -l information.txt. Who owns that file? What primary group does that file belong to? - Issue the command
su -to login to your root account. - Issue the following command to create a group called welcome:
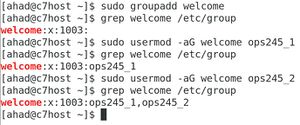
groupadd welcome - Issue the command:
grep welcome /etc/groupfile to confirm that the group welcome was created. - Read the man page for the
usermodcommand. Which option allow you to set the Group ID number (GID) when you create a new group? Which options allow you to both append and assign users to an existing group name? - Issue two separate usermod commands to add both ops235_1 and ops235_2 to the newly-created welcome group.
- Verify that both ops235_1 and ops235_2 now belong to the welcome group.
Practical Example
Management has sent you (the Linux systadmin) that a "new" employee has been hired and will be on on probation for 3 months. As the Linux system administrator, they want you to perform the following steps:
- Remain in your centos1 VM for this section.
- Use the useradd command to create a user account called: noobie to expire in 3 months from this date as part of the security policy of this organization (issue man useradd to determine correct option to set expiry date).
- Set an appropriate password for this user account.
- Add this newly-created user to the newly-created welcome group.
- Examine
/etc/groupto verify that you made the correct operations. - Use the usermod command to set the full name of the user account noobie to "Really Green". Examine the result of running that command in the
/etc/passwdfile. What has changed?
Unfortunately, you were later informed that this "noobie" employee was caught stealing from the company. They want you to perform the following operations: - Remove this account, but keep "noobie's" home directory for police investigation purposes.
- Verify that you correctly issued the correct commands.
Answer INVESTIGATION 1 observations / questions in your lab log book.
INVESTIGATION 2: Managing System Services and Run-levels
Part 1: How do we Manage System Services?
At the beginning of this lab we mentioned that running unneeded packages can be a security risk due to the unnecessary increase in the complexity of your system. Similarly, it is also unnecessarily hazardous, and even more so, to leave unneeded services running. In this investigation, we will learn how to control services, and turn off those services that we think are not necessary to help reduce security risks.
Although there is a command called: service that may appear to manager services on your Linux system, it is considered deprecated (i.e. "obsolete"). It has been replaced by using the systemctl command.
- Perform the following steps:
- Remain in your centos1 VM for this section.
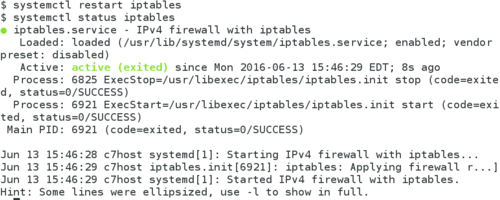
- To verify the status of your iptables service, issue the following command:
systemctl status iptables - Use the commands you used in Lab2 to stop and disable the iptables service.
- Issue a command to verify you disabled and stopped the iptables service.
Note: There is a major difference between stopping a service and disabling a service: If a service is stopped but enabled, the service will start upon reboot. Therefore to prevent it being started upon boot-up, the service will need to be disabled as well! - Issue the commands to start and enable the iptables service, and verify that it is started and enabled.
Note: If you performed the commands correctly, the iptables service should be running, and will automatically run upon your Linux machine start-up.
Part 2: How do we Manage Runlevels?
Running Linux servers in graphical mode can make the server vulnerable to penetration (i.e. a potential break-in to the server from unauthorized intruders). The X-windows framework can be vulnerable to attacks when these servers are connected to the Internet. This is why when you install server versions of Linux, they work in text-based mode only. Desktop versions of Linux are then installed on workstations (working in graphical mode) that connect to the Linux server (for security reasons since those servers are closest to the router and the Internet).
The Linux sysadmin can also change the run-level (or state) of a graphical Linux server to run in text-based mode and run the graphical mode by issuing a command when graphic mode is required. The run-level term is now deprecated in Fedora, and will likely be deprecated in RHEL/CentOS at some point as well, but for now this is what the industry is using.
- Perform the following steps:
- Remain in your centos1 VM for this section.
- Issue the following Linux command:
runlevel
Note: You should see two separate characters (like N 5). The number on the right is the current run-level 5 (which is graphical mode). The number or character on the left if the previous run level (which is N which means there was no previous run level since it was a "new" install). - You can use the init command to change the current run-level. See a list of runlevels here.
- Issue the init command to change the current run-level in centos1 to 3 by issuing the following command:
init 3 - What did you notice?
- Issue the following Linux command:
startx
What happens? Why would you want to make a graphical Linux system run in text-based mode? - Log-off your graphical system. You should return to your CLI shell prompt and change to root user. You should notice at this point that the command startx did not reset your run-level.
- Reissue the init command to change the current run-level back to 5
Did it work? - Issue the runlevel command to verify that the run-level is set to 5 (i.e. Graphical). You should notice a 3 followed by a 5. That is to indicate that the current run-level is 5, but previously, it was set to 3.
Answer INVESTIGATION 2 observations / questions in your lab log book.
INVESTIGATION 3: CREATING USERS VIA SHELL SCRIPTS
Using getopts Function & case statement
We will now use shell scripting to help automate the task for a Linux adminstrator to create regular user accounts.
- Perform the following steps:
- You will be using your c7host machine for this section.
- Open a shell terminal, and login as root.
- Change to the /root/bin directory.
- Download, study, and run the following shell script. Issue the command:
wget https://ict.senecacollege.ca/~ops235/labs/user-create.bash - Try to understand what these Bash Shell scripts do, and then run the script as root to create just one user called test. After running the shell script, view the contents of the /home directory to confirm.
Although the zenity command is a "user-friendly" way to run shell scripts, Linux administrators usually create shell scripts that resemble common Linux commands. In this lab, you will learn to create a shell script using the getopts function to make your shell script behave more like actual Linux commands (including the use of options). Refer to the notes section on the right-hand-side for reference about the case statement and the getopts function.
- Open a Bash shell terminal and login as root.
- Change to the /root/bin directory.
- Use the wget command to download the input file called user-data.txt by issuing the command:
wget https://ict.senecacollege.ca/~ops235/labs/user-data.txt - View the contents on the user-data.txt file to confirm there are 3 fields (username, fullname, and e-mail address)which are separated by the colon (:) symbol.
- Use a text editor (such as
viornano) to create a Bash Shell script called:createUsers.bashin the /root/bin directory. - Enter the following text content into your text-editing session:
#!/bin/bash
# createUsers.bash
# Purpose: Generates a batch of user accounts (user data stored in a text file)
#
# USAGE: /root/createUsers.bash [-i {input-path}]
#
# Author: *** INSERT YOUR NAME ***
# Date: *** CURRENT DATE ***
# Make certain user is logged in as root
if [ $USER != "root" ]
then
echo "Note: You are required to run this program as root."
exit 1
fi
if [ "$#" -eq 0 ] # if no arguments after command
then
echo "You must enter an argument" >&2
echo "USAGE: $0 [-i {input-path}]" >&2
exit 2
fi
- Save your editing session, but remain in the text editor.
- The code displayed below uses the getopt function set the input file pathname or check for invalid options or missing option text. Add the following code
outputFlag="n"
while getopts i: name
do
case $name in
i) inputFile=$OPTARG ;;
:) echo "Error: You need text after options requiring text"
exit 1 ;;
\?) echo "Error: Incorrect option"
exit 1 ;;
esac
done
- Save your editing session, but remain in the text editor.
- The code displayed below uses logic to exit the script if the input file does not exist. Command substitution is used to store each line of the input file as a positional parameter. There is one subtle problem here: The full names of the users contain spaces which can create havoc when trying to set each line as a separate positional parameter. In this case the sed command is used to convert spaces to plus signs (+), which will be converted back later. Finally, a for loop is used to create each account (useradd) and mail the user their account information (mail). Add the following code:
if [ ! -f $inputFile ]
then
echo "The file pathname \"$inputFile\" is empty or does not exist" >&2
exit 2
fi
set $(sed 's/ /+/g' $inputFile) # temporarily convert spaces to + for storing lines as positional parameters
for x
do
userPassWd=$(date | md5sum | cut -d" " -f1)
useradd -m -c "$(echo $x | cut -d":" -f2 | sed 's/+/ /g')" -p $userPassWd $(echo $x | cut -d":" -f1)
mail -s "Server Account Information" $(echo $x | cut -d":" -f3) <<+
Here is your server account information:
servername: myserver.senecac.on.ca
username: $(echo $x | cut -d":" -f1)
password: $userPassWd
Regards,
IT Department
+
done
echo -e "\n\nAccounts have been created\n\n"
exit 0
- Save, set permissions, and then run that shell script for the input text file user-data.txt. Did it work? Try running the script without an argument - What did it do?
- You have completed lab4. Proceed to Completing The Lab, and follow the instructions for "lab sign-off".
Answer INVESTIGATION 3 observations / questions in your lab log book.
LAB 4 SIGN-OFF (SHOW INSTRUCTOR)
Exclusively for Summer 2020 term, submissions are accepted only online!
Follow the submission instructions for lab 4 on Blackboard.
- Perform the Following Steps:
- Make certain that your c7host, centos1 and centos2 VMs are running.
- Switch to your c7host VM.
- Open a shell terminal, su - into root, and change to the /root/bin directory.
- Issue the Linux command:
wget https://ict.senecacollege.ca/~ops235/labs/lab4-check.bash - Give the lab4-check.bash file execute permissions (for the file owner).
- Run the shell script and if any warnings, make fixes and re-run shell script until you receive "congratulations" message.
- Arrange proof of the following on the screen:
✓ centos1 VM:
✓c7host machine- Demonstrate that this VM 's current run-level is set to 5.
✓ Lab4 log-book filled out.- Run the lab4-check.bash script in front of your instructor (must have all
OKmessages)
Practice For Quizzes, Tests, Midterm & Final Exam
- Describe all of the field in
/etc/passwd - What is the command to create a user? What option to create a home directory for that user?
- What is the command to change the full name of an already-created user?
- What is the command to delete a user account? What option allows for the user's home directory to be removed as well?
- What is the command to create a group? What is the command (or steps) to include a user in a newly-created group?
- What is the purpose of
/etc/shadow? - What is the purpose of
/etc/skel? - What does the term run-level mean?
- How to set the run-level of a Linux system to text-based only? How to set to graphical mode?
- What is the command to view the status of running services?
- What is the command to start a service (like httpd, or sshd)?
- What is the command to stop a service (like httpd, or sshd)?
- What is the difference between starting a service and enabling a service?
- Can a service be stopped and started by issuing just one command?
- What is the purpose of the case statement in shell scripting?
- What is the purpose of the getopts function in shell scripting?
- What type of shell script would be best to automatically create 1200 user accounts (which a list of usernames are stored in a text-file)?