Difference between revisions of "OPS335 Lab 3"
Ahadalioglu (talk | contribs) m (→Installation) |
|||
| (90 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category:OPS335]][[Category:OPS335 Labs]] | [[Category:OPS335]][[Category:OPS335 Labs]] | ||
| − | |||
| − | |||
| − | In this lab, you will configure a Linux machine to be a DNS server for the rest of the machines in your Intranet. You will '''use <u>your</u> MySeneca ID as your domain'''. The server will handle all queries for names in the '''yoursenecaid. | + | == OBJECTIVE & PREPARATION== |
| + | In this lab, you will configure a Linux machine to be a DNS server for the rest of the machines in your Intranet. You will '''use <u>your</u> MySeneca ID (the one based on your name, not your student number) as your domain'''. The server will handle all queries for names in the '''yoursenecaid.ops''' domain. The server will also pass DNS queries for other names and addresses out to the Internet (i.e. to Seneca's DNS server). | ||
| + | |||
| + | === Online Resources=== | ||
| + | |||
| + | * [https://en.wikipedia.org/wiki/Domain_Name_System#Address_resolution_mechanism Address resolution mechanism] | ||
| + | * [https://en.wikipedia.org/wiki/Reverse_DNS_lookup Reverse DNS lookups] | ||
| + | |||
| + | === Current Configuration === | ||
| + | |||
This is the current state of our internal network when your harddrive is plugged into a lab machine. Please note that if any of the listed services aren't working for you, you should then fix them (especially your iptables which may block DNS traffic needed for this lab): | This is the current state of our internal network when your harddrive is plugged into a lab machine. Please note that if any of the listed services aren't working for you, you should then fix them (especially your iptables which may block DNS traffic needed for this lab): | ||
| Line 15: | Line 22: | ||
| − | After you have completed this lab, your ''' | + | After you have completed this lab, your '''host''' VM will be running a full-featured DNS server (which is how you're going to get the '''yoursenecaid.ops''' domain without paying for it). Unfortunately, you will be the only one using your DNS server so no-one else will be able to resolve hosts under '''yoursenecaid.ops''' |
| + | === How DNS resolution works === | ||
| − | + | We will review in class how the Domain Name Service works. You should also read in your own time [https://en.wikipedia.org/wiki/Domain_Name_System#Address_resolution_mechanism the DNS article on Wikipedia] for an overview of a DNS query - especially the Address resolution mechanism section (including the '''Recursive''' and '''caching name server''' subsections). The diagram shown in the WIKI is also quite simple and easy to understand. Domain Name Service is a LARGE topic but this lab provides the basic principles and essentials for this course and DNS set-up for other courses. | |
| − | |||
| − | We will review in class how the Domain Name Service works. You should also read in your own time | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
= INVESTIGATION 1: CONFIGURING THE DNS SERVER = | = INVESTIGATION 1: CONFIGURING THE DNS SERVER = | ||
| − | We will now be '''installing, configuring and running a DNS server on our | + | We will now be '''installing, configuring and running a DNS server on our host'''. In most networks, the gateway would '''not''' also be a DNS server, |
| + | but if we placed ours on a separate virtual machine we would need that VM to always be running in order for the other VMs to retrieve updates, install software, or even communicate with each other. | ||
== Preparation == | == Preparation == | ||
| − | First, ensure that the '''host''' and '''vms''' are running, and | + | First, ensure that the '''host''' and '''vms''' are running, and that none of your machines have entries for the host or any of the VMs in /etc/hosts. In previous courses you may have relied on the contents of /etc/hosts but you will not use them in this course so that you can see how vital a properly functioning DNS server is. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== Installation == | == Installation == | ||
| − | Install | + | Install '''bind''' on your '''host''' machine. |
== Configuration == | == Configuration == | ||
| Line 56: | Line 47: | ||
=== /etc/named.conf === | === /etc/named.conf === | ||
| − | When you install Bind you'll get a default '''/etc/named.conf'''. | + | When you install Bind you'll get a default '''/etc/named.conf'''. Copy this file over to a backup location and empty the original (If you have SELinux enabled - do not delete or move the file as that will cause SELinux not to trust it). We will be writing one from scratch with only the following contents, but use your own XX value where applicable. |
<pre> | <pre> | ||
options { | options { | ||
directory "/var/named/"; | directory "/var/named/"; | ||
| − | allow-query {127.0.0.1; 192.168. | + | allow-query {127.0.0.1; 192.168.XX.0/24;}; |
| − | forwarders { | + | forwarders { 208.67.222.222; }; # This one works at home |
| + | #forwarders { 10.102.100.21; }; # This one works at Seneca | ||
}; | }; | ||
zone "localhost" { | zone "localhost" { | ||
| Line 68: | Line 60: | ||
file "named.localhost"; | file "named.localhost"; | ||
}; | }; | ||
| − | zone "yoursenecaid. | + | zone "yoursenecaid.ops" { |
type master; | type master; | ||
| − | file "mydb-for-yoursenecaid- | + | file "mydb-for-yoursenecaid-ops"; |
}; | }; | ||
</pre> | </pre> | ||
| Line 81: | Line 73: | ||
* '''type''' | * '''type''' | ||
* '''file''' | * '''file''' | ||
| + | |||
| + | Note: If you are using a drive an a removable bay, you will need to set the forwarders address differently. Pick any one of the DNS servers that are provided through DHCP. | ||
=== Zone file === | === Zone file === | ||
| − | Now edit '''/var/named/mydb-for-yoursenecaid- | + | Now edit '''/var/named/mydb-for-yoursenecaid-ops''' and enter the following (use your own XX value and domain where applicable). |
<pre> | <pre> | ||
$TTL 3D | $TTL 3D | ||
| − | @ IN SOA | + | @ IN SOA host.yoursenecaid.ops. hostmaster.yoursenecaid.ops.( |
| − | + | 2018042901 ; Serial | |
8H ; Refresh | 8H ; Refresh | ||
2H ; Retry | 2H ; Retry | ||
1W ; Expire | 1W ; Expire | ||
1D ; Negative Cache TTL | 1D ; Negative Cache TTL | ||
| − | + | ); | |
| − | @ IN NS | + | @ IN NS host.yoursenecaid.ops. |
| − | + | host IN A 192.168.XX.1 | |
</pre> | </pre> | ||
| Line 110: | Line 104: | ||
# Check that the ''named'' service is running using the '''ps ax''' command (perhaps combined with '''grep'''), and separately, the '''systemctl''' command (if necessary), or check the '''/var/log/messages''' file for troubleshooting purposes. | # Check that the ''named'' service is running using the '''ps ax''' command (perhaps combined with '''grep'''), and separately, the '''systemctl''' command (if necessary), or check the '''/var/log/messages''' file for troubleshooting purposes. | ||
# Once you are certain that the ''named'' service had started and runs without errors, then set it to '''start automatically''' (i.e. enable the named service) when this virtual machine boots. | # Once you are certain that the ''named'' service had started and runs without errors, then set it to '''start automatically''' (i.e. enable the named service) when this virtual machine boots. | ||
| − | # You also need to set | + | # You also need to set it self '''(127.0.0.1)''' as the primary domain name server ('''DNS1''') for your '''host''' machine to your '''host machine's ifcfg file''' <br /> |
| + | # If your host's external facing interface (ens33) is on DHCP, you will need to also add PEERDNS=NO to ifcfg file to prevent DHCP server from assigning the original DNS server (i.e. 192.168.40.2 which is used as forwarder instead by the DNS server you are setting up) <br /><br />'''NOTE:''' You should know how to do that, but if you forgot the procedure, refer to [http://zenit.senecac.on.ca/wiki/index.php/OPS335_Lab_1#Making_Persistent_.28Permanent.29_Network_Setting_Changes Lab 1].<br><br> | ||
| + | # Now that you know the service works, '''add the resource records necessary for it to provide forward lookups of the other machines in your virtual network''' (hint: You should only need three more records) and restart the service. | ||
| + | == Firewall rules update == | ||
| − | + | Remember that you are supposed to have a working firewall on your '''host''' (and every other machine), but we will focus on our '''host''' machine for now. A <u>working</u> firewall will block requests to ports that you didn't explicitly allow. This means that at this point, your DNS server, even though it's perfectly configured, is <u>'''inaccessible'''</u> to any other machine because iptables won't allow the requests to come in (the machine can communicate with itself using the rule that allows all traffic on the '''lo''' interface). | |
| − | + | '''Perform the Following Steps:''' | |
| − | + | # Note: Since you are going to save your firewall at the end of this step, you may wish to '''stop libvirtd''' and '''restart iptables''' now in order to avoid saving the rules the libvirtd automatically adds to your INPUT, FORWARD, and POSTROUTING chains. | |
| + | # You will need to update the firewall on '''host''' to allow <u>incoming</u> connections to '''port 53 for both UDP and TCP''' (i.e. the protocol and port that DNS uses). | ||
| + | # After you have updated your firewall, save your iptables rules. | ||
| + | # <b>Once you rules are saved, restart libvirtd to ensure NAT and forwarding rules are re-added.</b> | ||
| − | + | '''NOTE:''' You could just disable the firewall '''but that is a poor workaround!''' You are expected to be able to handle configuration (such as this) at this point in this course. | |
| − | |||
| − | You could just disable the firewall but that is a poor workaround! You are expected to be able to handle configuration (such as this) at this point in this course. | ||
'''Record steps, commands, and your observations in INVESTIGATION 1 in your OPS335 lab log-book''' | '''Record steps, commands, and your observations in INVESTIGATION 1 in your OPS335 lab log-book''' | ||
| − | |||
= INVESTIGATION 2: CONFIGURING THE DNS CLIENT = | = INVESTIGATION 2: CONFIGURING THE DNS CLIENT = | ||
| − | Before proceeding, we need to set the primary DNS server (DNS1 ) in your '''ifcfg-eth0''' (or ''ifcfg-en0'') file for your network interface cards for your virtual machines. Also it is a good idea to install the '''bind-utils''' package on those | + | Before proceeding, we need to set the primary DNS server (DNS1 ) in your '''ifcfg-eth0''' (or ''ifcfg-en0'') file for your network interface cards for your virtual machines. Also it is a good idea to install the '''bind-utils''' package on those VMs as well in order to perform queries on your host domain name server. |
'''Perform the following Steps:''' | '''Perform the following Steps:''' | ||
| − | # | + | #Install the '''bind-utils''' package for your virtual machines. |
| − | #You will need to configure your | + | #You will need to configure your VMs to use your host's IPADDR as the '''default DNS server''' (DNS1) in your '''ifcfg-eth0''' (or ''ifcfg-en0'') file for your network interface card.<br>You should know how to do that, but if you forgot the procedure, refer to [http://zenit.senecac.on.ca/wiki/index.php/OPS335_Lab_1#Making_Persistent_.28Permanent.29_Network_Setting_Changes Lab 1]. |
| + | #Modify the hostname of '''each machine''' (host and all three VMs) to match what the DNS server says it is (including the domain). This will be important for services we configure in later labs. | ||
| − | + | == Testing == | |
| − | + | '''Perform the Following Steps:''' | |
| − | + | <ol><li>Issue the following commands to verify that you set-up your DNS server correctly on all of your VMs and google and your host machine: | |
| + | <source> | ||
| + | host vm1.yoursenecaid.ops | ||
| + | host vm2.yoursenecaid.ops | ||
| + | host vm3.yoursenecaid.ops | ||
| + | host host.yoursenecaid.ops | ||
| + | host google.ca</source></li> | ||
| − | + | <li>Also try the following commands: | |
| + | <source> | ||
| + | host vm1 | ||
| + | host vm2 | ||
| + | host vm3 | ||
| + | host host | ||
| + | </source> | ||
| − | + | {{Admon/important |Host Command Doesn't Work|Your machines do not know what domain to automatically add to the end of hostnames (or believe they are still in the seneca domain). The '''SEARCH''' (or DOMAIN) parameter in the '''ifcfg-eth0''' file is used to specify your own domain (eg. '''yoursenecaid.ops''' ).<br><br>}} | |
| − | + | <li> Add the '''SEARCH''' (or DOMAIN) parameter for your '''ifcfg-eth0''' file as shown above for your '''host''' machine.</li> | |
| − | + | <li> Issue the '''host''' command for all vm names and host name to make certain that is works.</li> | |
| − | + | <li>Also on all of the VMs, install and use a text-based browser called '''lynx''' to access the Web, and test-out to see if it works by issuing the command '''lynx''' with the URL as an argument.</li><li>Experiment with the following commands:<br> | |
| − | + | <source> | |
| − | |||
| − | |||
| − | |||
| − | <source | ||
nslookup | nslookup | ||
| − | dig</source>Use the '''dig''' command to query your DNS server for specific records (up to this point you only have NS and | + | dig</source>Use the '''dig''' command to query your DNS server for specific records (up to this point you only have NS, A, and SOA records).</li></ol> |
| + | |||
| + | '''Record steps, commands, and your observations in INVESTIGATION 2 in your OPS335 lab log-book''' | ||
| + | |||
| + | = INVESTIGATION 3: CONFIGURING THE DNS SERVER FOR REVERSE LOOKUPS = | ||
| + | |||
| + | As it stands now, your server will only handle forward resolution (converting names into addresses), but it is also sometimes necessary to convert addresses back into human readable names. For public IP addresses only your ISP can provide this service for you. For private networks you can set it up for your own organisation. But even if you're setting up reverse DNS on the public internet - you need to understand what information the ISP would require. | ||
| + | |||
| + | Issue the following commands on any of your VMs (once again replacing XX with your network octet): | ||
| + | |||
| + | <source> | ||
| + | host 192.168.XX.1 | ||
| + | host 192.168.XX.2 | ||
| + | host 192.168.XX.3 | ||
| + | host 192.168.XX.4</source> | ||
| + | |||
| + | Each one should have failed because there is currently nothing that will handle this reverse lookup for you. This requires another zone on your server. | ||
| + | |||
| + | Add the following entry to your '''/etc/named.conf''' (once again replacing XX with your own octet): | ||
| + | |||
| + | <pre> | ||
| + | zone "XX.168.192.in-addr.arpa." { | ||
| + | type master; | ||
| + | file "mydb-for-192.168.XX"; | ||
| + | }; | ||
| + | </pre> | ||
| + | And create the following zone file: | ||
| − | + | <pre> | |
| + | $TTL 3D | ||
| + | @ IN SOA host.yoursenecaid.ops. hostmaster.yoursenecaid.ops.( | ||
| + | 2018042901 ; Serial | ||
| + | 8H ; Refresh | ||
| + | 2H ; Retry | ||
| + | 1W ; Expire | ||
| + | 1D ; Negative Cache TTL | ||
| + | ); | ||
| + | @ IN NS host.yoursenecaid.ops. | ||
| + | 1 IN PTR host.yoursenecaid.ops. | ||
| + | </pre> | ||
| − | ''' | + | <ol><li>Refer to the [http://www.zytrax.com/books/dns/ch8/ptr.html reference documentation] for '''PTR''' records.</li> |
| + | <li>Add the extra records needed to complete this zone (again, you should only need three more).</li> | ||
| + | <li>Restart the service and test these records to make sure they work.</li> | ||
| + | </ol> | ||
| + | {{Admon/important |Backup your VMs!|You MUST perform a '''full backup''' of ALL of your VMs whenever you complete your '''OPS335 labs''' or when working on your '''OPS335 assignments'''. You should be using the dump or rsync command, and you should use the Bash shell script that you were adviced to create in order to backup all of your VMs.}} | ||
= COMPLETING THE LAB = | = COMPLETING THE LAB = | ||
| Line 168: | Line 215: | ||
You have now gained experience with some common configuration settings for named, as well as common resource records. | You have now gained experience with some common configuration settings for named, as well as common resource records. | ||
| + | ===Online Submission=== | ||
| + | Follow the instructions for lab 3 on blackboard. | ||
| + | <!-- | ||
| + | ===Andrew's sections=== | ||
| + | |||
| + | You may choose to: | ||
| + | * Submit screenshots of your work on Blackboard, in which case you don't need to come to the lab. | ||
| + | * Or come to the lab, show me your work, and talk to me about it. I want to hear what you've learned and answer any questions you have. | ||
| − | ' | + | You'll get the same grade regardless of how you choose to submit your work. |
| − | ::<span style="color:green;font-size:1.5em;">✓</span>Comment out the hostname resolution (/etc/hosts) files for ALL vms, and use '''host''' command to query from a VM, the IPADDR for:<br>'''vm1.yoursenecaid. | + | Expected results of this lab are: |
| − | ::<span style="color:green;font-size:1.5em;">✓</span>'''nslookup''' information ('''A''', '''NS''', '''MX''' records) for '''vm1.yoursenecaid. | + | ::<span style="color:green;font-size:1.5em;">✓</span>Comment out the hostname resolution (/etc/hosts) files for ALL vms, and use '''host''' command to query from a VM, the IPADDR for:<br><blockquote>'''host.yoursenecaid.ops''' , '''vm1.yoursenecaid.ops''' , '''vm2.yoursenecaid.ops''' , and '''vm3.yoursenecaid.ops'''</blockquote> |
| − | ::<span style="color:green;font-size:1.5em;">✓</span>'''dig +trace''' for '''vm1.yoursenecaid. | + | ::<span style="color:green;font-size:1.5em;">✓</span>'''nslookup''' information ('''A''', '''NS''', '''MX''' records) for:<br><blockquote>'''host.yoursenecaid.ops''' , '''vm1.yoursenecaid.ops''' , '''vm2.yoursenecaid.ops''' , '''vm3.yoursenecaid.ops'''.</blockquote> |
| + | ::<span style="color:green;font-size:1.5em;">✓</span>'''dig +trace''' for:<br><blockquote>'''host.yoursenecaid.ops''' , '''vm1.yoursenecaid.ops''' , '''vm2.yoursenecaid.ops''' , '''vm3.yoursenecaid.ops'''.</blockquote> | ||
| + | ::<span style="color:green;font-size:1.5em;">✓</span>Download and run '''https://ict.senecacollege.ca/~andrew.smith/ops335/labcheck3.bash''' | ||
::<span style="color:green;font-size:1.5em;">✓</span>Completed Lab3 log-book notes. | ::<span style="color:green;font-size:1.5em;">✓</span>Completed Lab3 log-book notes. | ||
| + | --> | ||
=EXPLORATION QUESTIONS= | =EXPLORATION QUESTIONS= | ||
| Line 184: | Line 242: | ||
#What parameter did you set in that file to tell the machine to refer to your own DNS server? | #What parameter did you set in that file to tell the machine to refer to your own DNS server? | ||
#What is the purpose of the '''/etc/resolv.conf''' file? | #What is the purpose of the '''/etc/resolv.conf''' file? | ||
| − | |||
#What are type '''A''' records used for? | #What are type '''A''' records used for? | ||
#What security features are available for DNS? | #What security features are available for DNS? | ||
Latest revision as of 13:12, 8 February 2021
Contents
OBJECTIVE & PREPARATION
In this lab, you will configure a Linux machine to be a DNS server for the rest of the machines in your Intranet. You will use your MySeneca ID (the one based on your name, not your student number) as your domain. The server will handle all queries for names in the yoursenecaid.ops domain. The server will also pass DNS queries for other names and addresses out to the Internet (i.e. to Seneca's DNS server).
Online Resources
Current Configuration
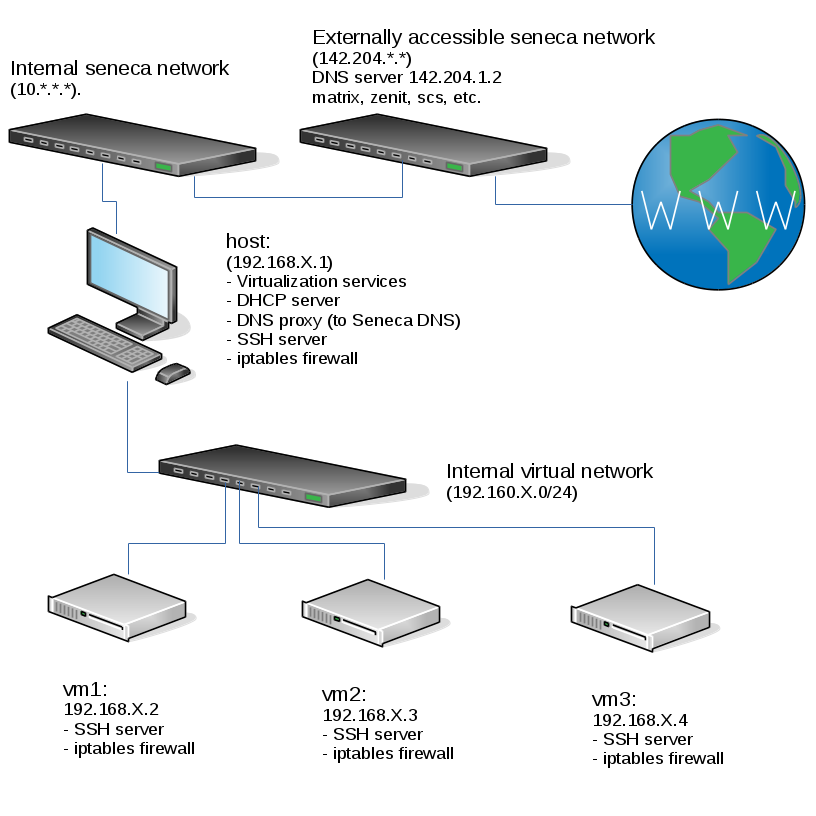
This is the current state of our internal network when your harddrive is plugged into a lab machine. Please note that if any of the listed services aren't working for you, you should then fix them (especially your iptables which may block DNS traffic needed for this lab):
You can see in the diagram above that when one of your VMs does a name resolution request:
- The VM contacts the host, which is running a DNS proxy (a.k.a. stub resolver), not a full DNS server
- The DNS proxy on the host contacts the Seneca DNS server, which was assigned to be used on the host via DHCP
- Depending on the type of request, the Seneca DNS server may contact other DNS servers to get an answer to the request.
After you have completed this lab, your host VM will be running a full-featured DNS server (which is how you're going to get the yoursenecaid.ops domain without paying for it). Unfortunately, you will be the only one using your DNS server so no-one else will be able to resolve hosts under yoursenecaid.ops
How DNS resolution works
We will review in class how the Domain Name Service works. You should also read in your own time the DNS article on Wikipedia for an overview of a DNS query - especially the Address resolution mechanism section (including the Recursive and caching name server subsections). The diagram shown in the WIKI is also quite simple and easy to understand. Domain Name Service is a LARGE topic but this lab provides the basic principles and essentials for this course and DNS set-up for other courses.
INVESTIGATION 1: CONFIGURING THE DNS SERVER
We will now be installing, configuring and running a DNS server on our host. In most networks, the gateway would not also be a DNS server, but if we placed ours on a separate virtual machine we would need that VM to always be running in order for the other VMs to retrieve updates, install software, or even communicate with each other.
Preparation
First, ensure that the host and vms are running, and that none of your machines have entries for the host or any of the VMs in /etc/hosts. In previous courses you may have relied on the contents of /etc/hosts but you will not use them in this course so that you can see how vital a properly functioning DNS server is.
Installation
Install bind on your host machine.
Configuration
An authoritative Bind server has a global configuration file (named.conf) and at least one zone file for the zone it's authoritative for.
/etc/named.conf
When you install Bind you'll get a default /etc/named.conf. Copy this file over to a backup location and empty the original (If you have SELinux enabled - do not delete or move the file as that will cause SELinux not to trust it). We will be writing one from scratch with only the following contents, but use your own XX value where applicable.
options {
directory "/var/named/";
allow-query {127.0.0.1; 192.168.XX.0/24;};
forwarders { 208.67.222.222; }; # This one works at home
#forwarders { 10.102.100.21; }; # This one works at Seneca
};
zone "localhost" {
type master;
file "named.localhost";
};
zone "yoursenecaid.ops" {
type master;
file "mydb-for-yoursenecaid-ops";
};
You need to understand all the options in this file except the localhost zone, so that in the future (for example in a practical test) you can quickly set up a DNS server for a new zone. So look up in the reference these things and write down what they do:
- directory
- allow-query
- forwarders
- type
- file
Note: If you are using a drive an a removable bay, you will need to set the forwarders address differently. Pick any one of the DNS servers that are provided through DHCP.
Zone file
Now edit /var/named/mydb-for-yoursenecaid-ops and enter the following (use your own XX value and domain where applicable).
$TTL 3D
@ IN SOA host.yoursenecaid.ops. hostmaster.yoursenecaid.ops.(
2018042901 ; Serial
8H ; Refresh
2H ; Retry
1W ; Expire
1D ; Negative Cache TTL
);
@ IN NS host.yoursenecaid.ops.
host IN A 192.168.XX.1
Again, here's the reference documentation for records in this file. Specifically pay attention to:
- A records
- NS records
- SOA records
Now that your DNS server (bind, a.k.a. named) is configured:
- Start the named service with the systemctl command.
- Check that the named service is running using the ps ax command (perhaps combined with grep), and separately, the systemctl command (if necessary), or check the /var/log/messages file for troubleshooting purposes.
- Once you are certain that the named service had started and runs without errors, then set it to start automatically (i.e. enable the named service) when this virtual machine boots.
- You also need to set it self (127.0.0.1) as the primary domain name server (DNS1) for your host machine to your host machine's ifcfg file
- If your host's external facing interface (ens33) is on DHCP, you will need to also add PEERDNS=NO to ifcfg file to prevent DHCP server from assigning the original DNS server (i.e. 192.168.40.2 which is used as forwarder instead by the DNS server you are setting up)
NOTE: You should know how to do that, but if you forgot the procedure, refer to Lab 1. - Now that you know the service works, add the resource records necessary for it to provide forward lookups of the other machines in your virtual network (hint: You should only need three more records) and restart the service.
Firewall rules update
Remember that you are supposed to have a working firewall on your host (and every other machine), but we will focus on our host machine for now. A working firewall will block requests to ports that you didn't explicitly allow. This means that at this point, your DNS server, even though it's perfectly configured, is inaccessible to any other machine because iptables won't allow the requests to come in (the machine can communicate with itself using the rule that allows all traffic on the lo interface).
Perform the Following Steps:
- Note: Since you are going to save your firewall at the end of this step, you may wish to stop libvirtd and restart iptables now in order to avoid saving the rules the libvirtd automatically adds to your INPUT, FORWARD, and POSTROUTING chains.
- You will need to update the firewall on host to allow incoming connections to port 53 for both UDP and TCP (i.e. the protocol and port that DNS uses).
- After you have updated your firewall, save your iptables rules.
- Once you rules are saved, restart libvirtd to ensure NAT and forwarding rules are re-added.
NOTE: You could just disable the firewall but that is a poor workaround! You are expected to be able to handle configuration (such as this) at this point in this course.
Record steps, commands, and your observations in INVESTIGATION 1 in your OPS335 lab log-book
INVESTIGATION 2: CONFIGURING THE DNS CLIENT
Before proceeding, we need to set the primary DNS server (DNS1 ) in your ifcfg-eth0 (or ifcfg-en0) file for your network interface cards for your virtual machines. Also it is a good idea to install the bind-utils package on those VMs as well in order to perform queries on your host domain name server.
Perform the following Steps:
- Install the bind-utils package for your virtual machines.
- You will need to configure your VMs to use your host's IPADDR as the default DNS server (DNS1) in your ifcfg-eth0 (or ifcfg-en0) file for your network interface card.
You should know how to do that, but if you forgot the procedure, refer to Lab 1. - Modify the hostname of each machine (host and all three VMs) to match what the DNS server says it is (including the domain). This will be important for services we configure in later labs.
Testing
Perform the Following Steps:
- Issue the following commands to verify that you set-up your DNS server correctly on all of your VMs and google and your host machine:
host vm1.yoursenecaid.ops host vm2.yoursenecaid.ops host vm3.yoursenecaid.ops host host.yoursenecaid.ops host google.ca
- Also try the following commands:
host vm1 host vm2 host vm3 host host
- Add the SEARCH (or DOMAIN) parameter for your ifcfg-eth0 file as shown above for your host machine.
- Issue the host command for all vm names and host name to make certain that is works.
- Also on all of the VMs, install and use a text-based browser called lynx to access the Web, and test-out to see if it works by issuing the command lynx with the URL as an argument.
- Experiment with the following commands:
Use the dig command to query your DNS server for specific records (up to this point you only have NS, A, and SOA records).nslookup dig
Record steps, commands, and your observations in INVESTIGATION 2 in your OPS335 lab log-book
INVESTIGATION 3: CONFIGURING THE DNS SERVER FOR REVERSE LOOKUPS
As it stands now, your server will only handle forward resolution (converting names into addresses), but it is also sometimes necessary to convert addresses back into human readable names. For public IP addresses only your ISP can provide this service for you. For private networks you can set it up for your own organisation. But even if you're setting up reverse DNS on the public internet - you need to understand what information the ISP would require.
Issue the following commands on any of your VMs (once again replacing XX with your network octet):
host 192.168.XX.1
host 192.168.XX.2
host 192.168.XX.3
host 192.168.XX.4Each one should have failed because there is currently nothing that will handle this reverse lookup for you. This requires another zone on your server.
Add the following entry to your /etc/named.conf (once again replacing XX with your own octet):
zone "XX.168.192.in-addr.arpa." {
type master;
file "mydb-for-192.168.XX";
};
And create the following zone file:
$TTL 3D
@ IN SOA host.yoursenecaid.ops. hostmaster.yoursenecaid.ops.(
2018042901 ; Serial
8H ; Refresh
2H ; Retry
1W ; Expire
1D ; Negative Cache TTL
);
@ IN NS host.yoursenecaid.ops.
1 IN PTR host.yoursenecaid.ops.
- Refer to the reference documentation for PTR records.
- Add the extra records needed to complete this zone (again, you should only need three more).
- Restart the service and test these records to make sure they work.
COMPLETING THE LAB
Upon completion of this lab you have a DNS server in your network and every virtual machine is using it to resolve internal and external hostnames. You have now gained experience with some common configuration settings for named, as well as common resource records.
Online Submission
Follow the instructions for lab 3 on blackboard.
EXPLORATION QUESTIONS
- What iptables rules apply to DNS?
- Under what circumstances does DNS use TCP vs UDP?
- What is a zone file and what is it used for?
- Name the zone files used in this lab, and their purpose.
- What file did you edit to set a static IP address?
- What parameter did you set in that file to tell the machine to refer to your own DNS server?
- What is the purpose of the /etc/resolv.conf file?
- What are type A records used for?
- What security features are available for DNS?