Difference between revisions of "Proxy"
| Line 38: | Line 38: | ||
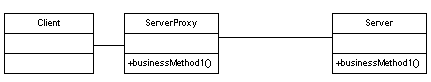
===UML Diagram=== | ===UML Diagram=== | ||
| − | [[Image:ProxyUML.gif| | + | [[Image:ProxyUML.gif|frame|UML Diagram for the Proxy Design Pattern]] |
==References== | ==References== | ||
Revision as of 18:50, 16 January 2007
The Proxy pattern is used in software development to create a placeholder for an object. The object is not actually created until the information that the object holds is required. This extra layer of abstraction saves time when a program must access a database or a disk for the information.
If the information is never required, the database/disk will never be queried and the system will run more efficiently with less slowdowns for unnecessary materializations.
Proxy Design Pattern
When a request is made to a Proxy, the real object is then instantiated. From then on, any further requests are made to the real object. There are four common situations where a Proxy pattern is required:
- Remote Proxy - provides a local representative that is located in a different address space.
- Virtual Proxy - creates expensive objects only when that object's information is required.
- Protection Proxy - provides access controls for different clients to a specified target object.
- Smart Reference Proxy - performs additional actions when a specific object is referenced such as counting the number of references, loading an object into memory when first referenced, and checking that the object is locked before access so that no other object may change it.
There are several other Proxy pattern situations less common in design:
- Copy-on-Write Proxy
- Cache Proxy
- Firewall Proxy
- Synchronization Proxy
UML Diagram
References
- Wikipedia article on the Proxy Pattern
- Design Patterns - Proxy UML Diagram
- Gamma, E., Helm, R., Johnson, R., Vlissides, J. (1995). Design Patterns: Elements of Reusable Object-Oriented Software. Addison-Wesley. ISBN 0-201-63361-2
- Design Class Diagrams - Proxy UML Diagram