Difference between revisions of "OPS345 Lab 2"
(→AWS Networking) |
(→AWS Networking) |
||
| Line 13: | Line 13: | ||
== Security == | == Security == | ||
| − | '''You're working on the real inetnet now!''' In many previous courses you were working in VMs on your virtual machines, on private networks, where attackers couldn't get to your servers even if they were super-dedicated and qualified. That is not the case in this course. | + | '''You're working on the real inetnet now!''' In many previous courses you were working in VMs on your virtual machines, on private networks, where attackers couldn't get to your servers even if they were super-dedicated and qualified. That is not the case in this course. Now an attacker doesn't even need to know who you are and they can take over your server. |
The VMs and networks you create in this course are likely to be accessible by anyone on the planet. That means you ''have to'' think of security. | The VMs and networks you create in this course are likely to be accessible by anyone on the planet. That means you ''have to'' think of security. | ||
| Line 20: | Line 20: | ||
This is not a security course, but you should be able to understand that different parts of your system are susceptible to different types of attacks. The more components you configure with security in mind: the less likely you are to become a victim of an attack. | This is not a security course, but you should be able to understand that different parts of your system are susceptible to different types of attacks. The more components you configure with security in mind: the less likely you are to become a victim of an attack. | ||
| + | |||
| + | = VPC = | ||
| + | |||
| + | The general idea of '''cloud''' is that your servers and services are not physically located on the premises of your business, but somewhere else. Typically wherever you can rent cheaper computers. Cloud providers have the advantage of economies of scale and the great flexibility of resource assignment. When you're not using some component: someone else will pay to use it. So hardware isn't sitting idle getting old and wasting electricity. | ||
| + | |||
| + | VPC stands for '''Virtual Private Cloud'''. That means the resources you're using are not dedicated to you, but they are separated from other users by software configuration. For all but the most high-value targets that's secure enough. | ||
| + | |||
| + | Inside your private cloud you can have networks, file storage, compute (processing VMs), databases, etc. | ||
| + | |||
| + | Access to your resources from the outside is available through an '''Internet Gateway''', which does port forwarding. It is used even if your VMs have public IP addresses. That is done in order to simplify securing your resources. | ||
| + | |||
| + | If your software uses any resources from outside your AWS VPC: those will also connect via the Internet Gateway. | ||
| + | |||
| + | = Subnets = | ||
* VPCs, subnets | * VPCs, subnets | ||
Revision as of 03:22, 16 December 2021
Contents
THIS PAGE IS A DRAFT, NOT A REAL COURSE PAGE
The current schedule for OPS345 is here: OPS335_Weekly_Schedule
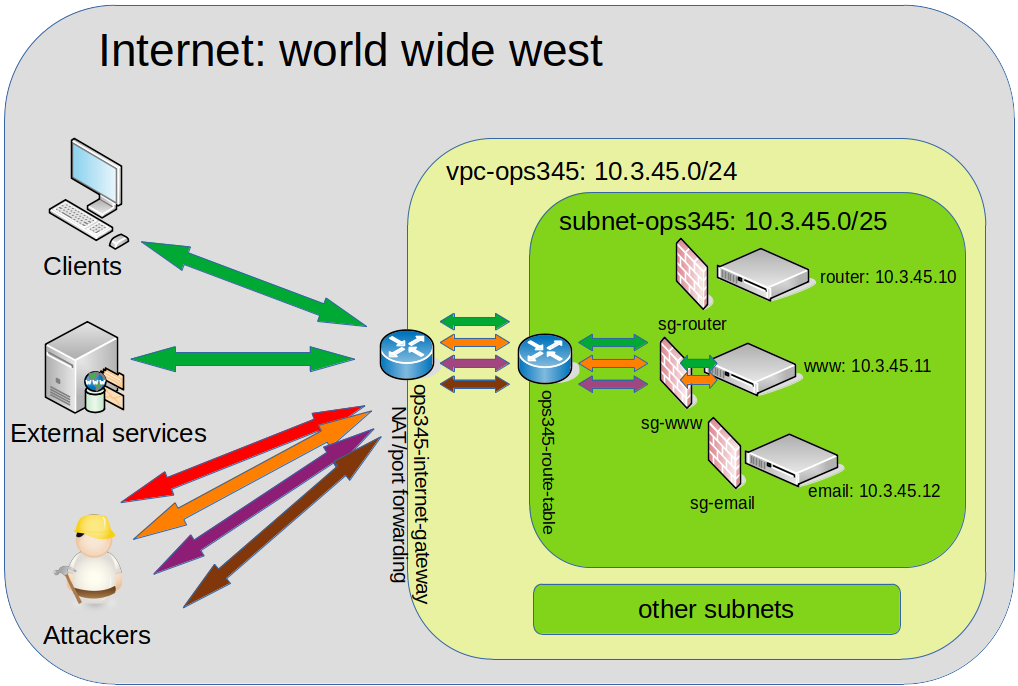
AWS Networking
The fundamentals you've learned about networking in your previous courses apply to AWS as well. The only difference from what you may be used to is that most of it is virtual in AWS. There are obviously still wires and cables and switches and routers, but their infrastructure has a layer of software on top to allow it to be more dynamic to deploy, configure, and use.
This diagram is a very simple overview of the parts of AWS networking you're going to use in this course:
Security
You're working on the real inetnet now! In many previous courses you were working in VMs on your virtual machines, on private networks, where attackers couldn't get to your servers even if they were super-dedicated and qualified. That is not the case in this course. Now an attacker doesn't even need to know who you are and they can take over your server.
The VMs and networks you create in this course are likely to be accessible by anyone on the planet. That means you have to think of security.
If you imagine that noone will attack your servers because you have nothing worth attacking: you're wrong. Every CPU connected to the internet is worth something. A most common scenario is an attacker (or organisation) finds a great number of vulnerable servers online, and make those part of a bot net. Then they will use the bot net they created (effectively a supercomputer) to launch attacks on targets that matter to them. They won't spend the time to attack your servers individually, but they have automation that exploits the most common security holes that lazy administrators leave open.
This is not a security course, but you should be able to understand that different parts of your system are susceptible to different types of attacks. The more components you configure with security in mind: the less likely you are to become a victim of an attack.
VPC
The general idea of cloud is that your servers and services are not physically located on the premises of your business, but somewhere else. Typically wherever you can rent cheaper computers. Cloud providers have the advantage of economies of scale and the great flexibility of resource assignment. When you're not using some component: someone else will pay to use it. So hardware isn't sitting idle getting old and wasting electricity.
VPC stands for Virtual Private Cloud. That means the resources you're using are not dedicated to you, but they are separated from other users by software configuration. For all but the most high-value targets that's secure enough.
Inside your private cloud you can have networks, file storage, compute (processing VMs), databases, etc.
Access to your resources from the outside is available through an Internet Gateway, which does port forwarding. It is used even if your VMs have public IP addresses. That is done in order to simplify securing your resources.
If your software uses any resources from outside your AWS VPC: those will also connect via the Internet Gateway.
Subnets
- VPCs, subnets
- Default dynamic public IP
- Default private network/IP
- Reserving a static public IP under "Elastic IPs", cost of doing that
- VPC dashboard:
- https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Internet_Gateway.html
- New VPC vpc-ops345 with CIDR block 10.3.45.0/24, no IPv6
- Subnets: create a new one in vpc-ops345 named subnet-ops345, in us-east-1a, 10.3.45.0/25 (to fit inside the VPC but leave room for other subnets later)
- Edit subnet, enable auto-assign public IPv4 addresses
- Internet Gateway: Create ops345-internet-gateway, attach to vpc-ops345
- Create new Route table ops345-route-table, add route for 0.0.0.0/0 through ops345-internet-gateway. Then add explicit subnet association to subnet-ops345
- Create a new security group "ops345sg" in vpc-ops345 with only the SSH port open.
- Create a new VM named "router", in the new vpc/subnet, with primary IP 10.3.45.10 (first 4 addresses on AWS subnet are not usable), default storage, ops345sg.
- Follow the instructions in lab 1 to set up your user, except use the subnet-ops345 and ops345sg and assign private ip 10.3.45.10. Also create a new key called ops345-all-aws-machines
- Note that "Auto-assign Public IP" is enabled by default, but don't change it.
- Wait till it starts, then go to "Elastic IPs" and associate an elastic IP with router. Call the elastic ip router_public_ip
- Name the network interface router-nic
Firewalls
- The purpose of a firewall on a server on the internet
- AWS Security Groups and iptables
iptables setup
- Install iptables-services, then enable and start the service (same as you did in OPS245).
- iptables fundamentals
- Securing services that need to be publicly accessible
Port forwarding SSH
- Create another VM the same way as "router" but without the elastic IP. Call it www. Name the network interface www-nic and set a secondary private IP to 10.3.45.11
- We won't set it up as a web server in this lab, we just need something to forward SSH requests to.
- firewall:
- iptables diagram source: https://documentation.suse.com/sles/15-SP1/html/SLES-all/cha-security-firewall.html
- forward incoming tcp port 2211 packets to port 22 on www
iptables -t nat -A PREROUTING -p tcp --dport 2211 -j DNAT --to 10.3.45.11:22
- allow forwarding to www (or just remove default reject rule)
iptables -D FORWARD 1
- perform ip masquerading
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
- trubleshooting
iptables -I FORWARD -j LOG tail -f /var/log/messages
- resulting firewall looks like this:
[root@router ~]# iptables -L -n Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination [root@router ~]# [root@router ~]# iptables -L -n -t nat Chain PREROUTING (policy ACCEPT) target prot opt source destination DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:2211 to:10.3.45.11:22 Chain INPUT (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0
- kernel:
vi /etc/sysctl.conf # add to the end: net.ipv4.ip_forward = 1 sysctl -p cat /proc/sys/net/ipv4/ip_forward
- test:
tcpdump -n -i eth0 port 2211
- aws:
- allow access to port 2211 in security group
- disable source/dest check for router in aws console (might not be necessary)
- Save the iptables rules when it looks like they're working.
~. will break out of locked up ssh session
Private security group
- Create a new security group "ops345sgprivate" to be used later for all VMs except the router.
- Add an inbound rule for ssh from ops345sg only