Difference between revisions of "Tutorial6: File Transfer / Sending Email Messages"
(→Sending Emails with Attachment (mail)) |
(→Sending Emails with File Attachment (mail)) |
||
| Line 94: | Line 94: | ||
===Sending Emails with File Attachment (mail)=== | ===Sending Emails with File Attachment (mail)=== | ||
| − | + | ''<span style="font-weight:bold;">mail</span> is a command-line email client for Unix and Unix-like operating systems.'' | |
=INVESTIGATION 1: USING SECURE COPY= | =INVESTIGATION 1: USING SECURE COPY= | ||
Revision as of 11:41, 27 January 2020
Contents
TRANSFERRING FILES / USING THE MAIL COMMAND
Main Objectives of this Practice Tutorial
- List common utilities combined with the ssh suite of utilities
- Securely copy files between Unix/Linux servers using the scp command
- Securely transfer copies of files between Unix/Linux servers using the sftp command
- Use the mail command to send email messages to your Seneca email account
- Use the mail command to send email with file attachments to your Seneca email account
Tutorial Reference Material
| Course Notes |
Definitions / Commands |
YouTube Videos | ||
| Course Notes: | Definitions: | File Transfer Commands: | Instructional Videos:
| |
KEY CONCEPTS
The ssh Linux command is actually a suite of tools to allow the user to not only issue commands securely between Unix / Linux servers, but also securely copy and transfer files among Unix/Linux servers via the commands scp and sftp.
In this tutorial, you will learn several different methods to securely transfer files from your Matrix Linux account to other computers
using Linux commands including scp, sftp and mail.
Secure Copy (scp)
Secure copy protocol (scp) is a means of securely transferring computer files between a local host and a remote host or between two remote hosts. It is based on the Secure Shell (SSH) protocol. "SCP" commonly refers to both the Secure Copy Protocol and the program itself.
Reference: https://en.wikipedia.org/wiki/Secure_copy
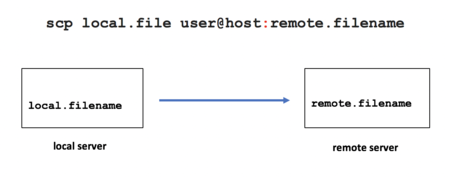
The usage for the scp command is similar to the cp command with the addition of host names, for example:
scp local.file user@host:destination-pathname
scp local.file user@host:
scp local.file host:
The most common mistake that students make is forgetting to add the colon character ":" after the remote hostname.
The user name in the command can be omitted if it's the same as on the local host.
Multiple file and recursive directory copy (i.e. option -R) is supported
Secure File Transmission Control Protocol (sftp)
sftp is a file transfer program, similar to ftp, which performs all operations over an encrypted ssh transport. It may also use many features of ssh, such as public key authentication and compression.
Reference: http://man7.org/linux/man-pages/man1/sftp.1.html
FTP is an acronym for File Transfer Protocol which provides a framework of rules on how to convert data that is transferred between computer servers (both identical and different).
When you login via the sftp command, you are in the sftp prompt (like a Bash shell prompt, but with a limited number of commands).
When issuing sftp commands it is important to understand that the local server relates to the server where you first issues the sftp command.
Below is a table that provides sftp commands to perform basic transfer and file management commands. Some of those commands loosely resemble Unix/Linux commands.
| Operation | sftp Command (Local Server) | sftp Command (Remote Server) |
|---|---|---|
| Display current working directory | !pwd | pwd |
| Display directory contents | !ls | ls |
| Change directory location | lcd | cd |
| Upload file to remote server | put | - |
| Download file to local server | get | - |
Sending Emails with File Attachment (mail)
mail is a command-line email client for Unix and Unix-like operating systems.
INVESTIGATION 1: USING SECURE COPY
In this section, you will learn how to ...
Perform the Following Steps:
- x
In the next investigation, you will ...
INVESTIGATION 2: USING SECURE TRANSMISSION CONTROL PROTOCOL
In this section, you will learn how to ...
Perform the Following Steps:
- x
In the next investigation, you will ...
INVESTIGATION 3: USING THE MAIL COMMAND
In this section, you will learn how to ...
Perform the Following Steps:
- x
LINUX PRACTICE QUESTIONS
The purpose of this section is to obtain extra practice to help with quizzes, your midterm, and your final exam.
Here is a link to the MS Word Document of ALL of the questions displayed below but with extra room to answer on the document to simulate a quiz:
https://ict.senecacollege.ca/~murray.saul/uli101/uli101_week6_practice.docx
Your instructor may take-up these questions during class. It is up to the student to attend classes in order to obtain the answers to the following questions. Your instructor will NOT provide these answers in any other form (eg. e-mail, etc).
Review Questions:
- x
- x
- x
- x
- x
- x
- x
- x
- Create a table listing each Linux command, useful options that were mentioned in the online assignment #1 and command purpose for the following Linux commands: scp , sftp , mail.