Difference between revisions of "SRT210 Lab 2"
(→PART 2: BASIC NETWORKING) |
(→PART 2: IPTABLES) |
||
| Line 78: | Line 78: | ||
* Use yum to uninstall firewalld and install iptables-services | * Use yum to uninstall firewalld and install iptables-services | ||
* Use systemctl to start the iptables service and configure it to be started on boot. | * Use systemctl to start the iptables service and configure it to be started on boot. | ||
| + | |||
| + | IPtables is a complex system, and there's a lot of material this week to cover it. Keep in mind as you're going through the lab that you're trying to learn three things: | ||
| + | |||
| + | * '''How iptables works''' | ||
| + | * '''How to understand the current state of the firewall''' | ||
| + | * '''How to make useful changes to the firewall''' | ||
| + | |||
| + | == IPtables overview == | ||
| + | |||
| + | We will use an example of setting up a firewall on a web server. | ||
| + | |||
| + | [[Image:iptables.png]] | ||
| + | |||
| + | '''There are some important things to be aware of in terms of this diagram:''' | ||
| + | |||
| + | :*There are '''<u>two sets</u> of IPtables rules (chains) that apply:''' '''OUTPUT/INPUT on the client''' and '''INPUT/OUTPUT on the server'''.<br>It is important to think about trafic from the perspective from the client as well as the server. | ||
| + | |||
| + | :* '''Outbound traffic is rarely blocked <u>unless</u> there is a security policy to <u>prevent</u> some kind of traffic'''.<br>Even in that case, that security policy is usually performed on a router. | ||
| + | |||
| + | :* '''Inbound traffic is of two distinct types'''. Our diagram shows: | ||
| + | ::# '''New incoming <u>connections</u>''' (what you normally think of as '''<u>inbound traffic</u>'''): the web server receives a '''new incoming connection'''. | ||
| + | ::# '''Incoming <u>data</u> that client receives as a response from the server''': the web page that the server sent back in the diagram above. | ||
| + | |||
| + | ::::The analogy would be like making a '''telephone call''':<ul><li>A '''NEW''' packet is like the phone ringing</li><li>An '''ESTABLISHED''' packet is the connection and the packet says "hello", along with any further communication.</li><li>A '''RELATED''' packet would be the same person calling on a second line. (eg. a second connection that is made because of something that happened in the first, like an ftp transfer).</li></ul> | ||
| + | |||
| + | ::::We normally don't want to do anything special for the response. It is safe to assume that '''a connection that was allowed to be established should be allowed to receive a response'''. This is accomplished with the following '''INPUT chain rule''' that should be there by default on your machines:<br> | ||
| + | ::::<pre>ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED</pre> | ||
| + | |||
| + | :* '''Rules are applied to:''' '''chains''' (e.g. ''input/output'') and contain information regarding the type of traffic they apply to. For example, '''protocols''' such as ''tcp/udp/icmp'', '''port numbers''' such as ''22 (SSH), 80 (HTTP), 443 (SHTTP)'', '''addresses''', and many other things. | ||
| + | |||
| + | ::Let's look at how these rules would apply to a simple web connection (HTTP - port 80): | ||
| + | ::# For the ''request'', the '''source port (sport) for the example in the above diagram is 40112''' and the '''destination port (dport) is 80''' | ||
| + | ::# For the ''response'', the '''source port (sport) is 80''' and the '''destination port (dport) is 40112''' | ||
| + | ::# Since the '''RELATED,ESTABLISHED''' rule already exists, we are only concerned about <u>'''controlling'''</u> the '''incoming traffic on the server''', which in our example, the '''chain is: INPUT''', the '''protocol is: tcp''', and the '''destination is: port 80'''. | ||
| + | |||
| + | :* 'Most other services work in a similar way as discussed above. | ||
Revision as of 10:17, 14 January 2019
Contents
Objectives
- Set up a nested virtual machine
- Get familiar with basic networking setup and utilities used on Linux
PART 1: NESTED VIRTUAL MACHINE
Since we're forced to use a Windows machine as the main VM host, we're going to have to set up nested virtualisation. Luckily that's not too difficult.
- Change the settings for your c7host to have at least 4GB of RAM, and enable "Virtual Intel VT-X/EPT or AMD-V/RVI" under VM/Settings/Processors.
- Install the following packages: qemu-kvm qemu-img virt-manager libvirt libvirt-python libvirt-client virt-install virt-viewer bridge-utils
- Make sure (using
systemctl enable) that the libvirtd service starts at boot. - Those will include both the KVM hypervisor and Virt Manager, which is a graphical tool used to administer it.
- Create a new virtual machine with the following settings:
- Will be installed from the network: https://mirror.senecacollege.ca/centos/7/os/x86_64/ or http://mirror.netflash.net/centos/7/os/x86_64/
- 2GB of RAM
- 10GB of disk
- NAT for networking
- hostname lin1
- Minimal install
After you're done - you'll have a command-line-only CentOS machine (lin1) running inside a graphical CentOS desktop (c7host).
PART 2: BASIC NETWORKING
Simple commands
Use these commands to check the curent network settings on lin1:
- ip link (show interfaces)
- ip address (the MAC address, IP address, and subnet mask for every interface)
- ip route (the routing table)
- cat /etc/resolv.conf (the DNS server you're configured to query)
- arp -n (the ARP table)
Note if you're missing a command - you can figure out what package contains in by using yum whatprovides
New virtual network
By default a KVM setup has a NAT network with a DHCP server. That works nicely out of the box but won't work for us because we'll need to configure network settings manually.
- Power off lin1
- In the Connection Details dialog box, select the Virtual Networks tab
- Click to de-select the Autostart (on boot) check-box options and click the Apply button.
- Stop the default network by clicking on the stop button at the bottom left-side of the dialog box.
- Click the add button to add a new network configuration.
- Leave the default network name network1.
- In the next screen, enter the new network IP address space called: 192.168.210.0/24
- Disable DHCPv4
- Enable Network Forwarding by Selecting Forwarding to physical network, the destination should be Any physical device and the mode should be NAT
Network settings on lin1
- Now if you try to start lin1 - it will tell you that the network "default" is unavailable. Go into the lin1 VM settings and configure the NIC to use "network1" instead.
- After starting the VM you'll find that your network interface is not configured (try all the commands above again to see their output).
- Configure your wired interface by editing the file .
- Change to the /etc/sysconfig/network-scripts directory.
- List the contents of this directory. You should see 2 different types of files, network config scripts and network configuration files.
- Look for the configuration file for your interface. It should have the name of the interface in the filename and the interface's MAC address in its contents.
- Edit that file and give it the following settings:
- DEVICE=eth0
- IPADDR=192.168.210.11
- NETMASK=255.255.255.0
- GATEWAY=192.168.210.1
- HWADDR=xx:xx:xx:xx:xx:xx # Make sure it's the right MAC address
- DNS1=192.168.210.1
- BOOTPROTO=static
- ONBOOT=yes
- NM_CONTROLLED=yes
- IPV6INIT=no
- Ask yourself where did the IP address 192.168.210.1 come from and why it's your default gateway and DNS server.
PART 2: IPTABLES
CentOS comes with firewalld installed by default. We will not be using that, instead we'll do all our firewall work with iptables. Therefore we'll need to uninstall firewalld and install iptables management tools:
- Use systemctl to stop firewalld and disable it from starting on boot.
- Use yum to uninstall firewalld and install iptables-services
- Use systemctl to start the iptables service and configure it to be started on boot.
IPtables is a complex system, and there's a lot of material this week to cover it. Keep in mind as you're going through the lab that you're trying to learn three things:
- How iptables works
- How to understand the current state of the firewall
- How to make useful changes to the firewall
IPtables overview
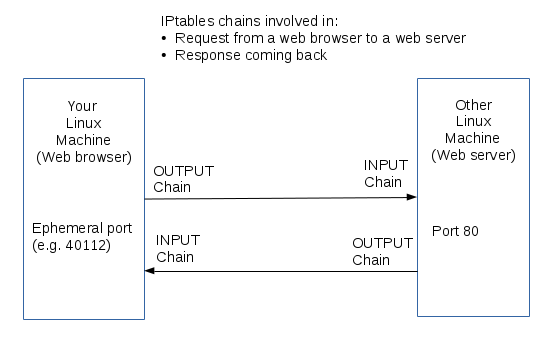
We will use an example of setting up a firewall on a web server.
There are some important things to be aware of in terms of this diagram:
- There are two sets of IPtables rules (chains) that apply: OUTPUT/INPUT on the client and INPUT/OUTPUT on the server.
It is important to think about trafic from the perspective from the client as well as the server.
- There are two sets of IPtables rules (chains) that apply: OUTPUT/INPUT on the client and INPUT/OUTPUT on the server.
- Outbound traffic is rarely blocked unless there is a security policy to prevent some kind of traffic.
Even in that case, that security policy is usually performed on a router.
- Outbound traffic is rarely blocked unless there is a security policy to prevent some kind of traffic.
- Inbound traffic is of two distinct types. Our diagram shows:
- New incoming connections (what you normally think of as inbound traffic): the web server receives a new incoming connection.
- Incoming data that client receives as a response from the server: the web page that the server sent back in the diagram above.
- The analogy would be like making a telephone call:
- A NEW packet is like the phone ringing
- An ESTABLISHED packet is the connection and the packet says "hello", along with any further communication.
- A RELATED packet would be the same person calling on a second line. (eg. a second connection that is made because of something that happened in the first, like an ftp transfer).
- The analogy would be like making a telephone call:
- We normally don't want to do anything special for the response. It is safe to assume that a connection that was allowed to be established should be allowed to receive a response. This is accomplished with the following INPUT chain rule that should be there by default on your machines:
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
- We normally don't want to do anything special for the response. It is safe to assume that a connection that was allowed to be established should be allowed to receive a response. This is accomplished with the following INPUT chain rule that should be there by default on your machines:
- Rules are applied to: chains (e.g. input/output) and contain information regarding the type of traffic they apply to. For example, protocols such as tcp/udp/icmp, port numbers such as 22 (SSH), 80 (HTTP), 443 (SHTTP), addresses, and many other things.
- Let's look at how these rules would apply to a simple web connection (HTTP - port 80):
- For the request, the source port (sport) for the example in the above diagram is 40112 and the destination port (dport) is 80
- For the response, the source port (sport) is 80 and the destination port (dport) is 40112
- Since the RELATED,ESTABLISHED rule already exists, we are only concerned about controlling the incoming traffic on the server, which in our example, the chain is: INPUT, the protocol is: tcp, and the destination is: port 80.
- Let's look at how these rules would apply to a simple web connection (HTTP - port 80):
- 'Most other services work in a similar way as discussed above.