Difference between revisions of "OPS335 DNS Lab"
(→Configuration) |
(→Zone file) |
||
| Line 106: | Line 106: | ||
#* The system log file /var/log/messages | #* The system log file /var/log/messages | ||
# Once you're sure the service starts and runs without errors - set it to start automatically when this virtual machine boots. | # Once you're sure the service starts and runs without errors - set it to start automatically when this virtual machine boots. | ||
| + | |||
| + | == Firewall rules update == | ||
| + | |||
| + | Remember you're supposed to have a working firewall on your vm1 (and every other machine, but this is the one we're concerned with now). A working firewall will block requests to ports that you didn't explicitly allow. Which means at this point your DNS server, even though it's perfetly configured, is inaccessible because iptables won't allow the requests to come in. | ||
| + | |||
| + | You'll need to update the firewall on vm1 to allow incoming connections in UDP port 53 - that's the protocol and port DNS works over. Then save your rules using whatever means worked for you in the iptables labs. | ||
| + | |||
| + | You can just disable the firewall but that is a poor workaround. You're expected to be able to handle configuration like this in this course. | ||
= INVESTIGATION 2: CONFIGURING DNS CLIENT = | = INVESTIGATION 2: CONFIGURING DNS CLIENT = | ||
Revision as of 01:13, 3 February 2016
Contents
DOMAIN NAME SYSTEM (DNS)
Lab goal
In this lab you will configure a Linux machine to be a DNS server for the rest of the machines in your intranet. You'll use your MySeneca ID as your domain. The server will handle all queries for names in the yoursenecaid.org domain. The server will pass DNS queries for other names and addresses out to the Internet (i.e. to Seneca's DNS server).
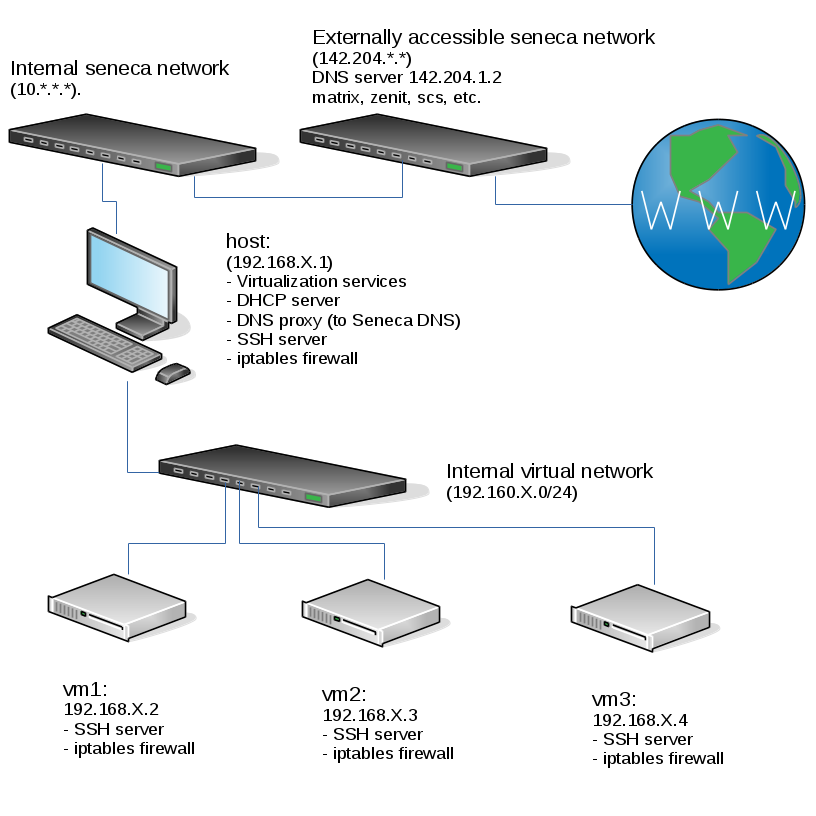
This is the current state of our internal network when your harddrive is plugged into a lab machine. Note that if any of the listed services aren't working for you - you should fix them (especially your iptables which may block DNS traffic needed for this lab):
You can see in the diagram above that when one of your VMs does a name resolution request:
- The VM contacts the host, which is running a DNS proxy (a.k.a. stub resolver), not a full DNS server
- The DNS proxy on the host contacts the Seneca DNS server, which was assigned to be used on the host via DHCP
- Depending on the request - the Seneca DNS server may contact other DNS servers to get the answer to the request.
After you're finished with this lab - your vm1 will be running a full-featured DNS server, which is how you're going to get the yoursenecaid.org domain without paying for it. Unfortunately you'll be the only one using your DNS server so noone else will be able to resolve hosts under yoursenecaid.org
How DNS resolution works
We'll go over this in class, but you should also read in your own time the Address resolution mechanism section (including the Recursive and caching name server subsection) on Wikipedia for an overview of a DNS query. The diagram there is also quite simple and appropriate. DNS is a large topic but this is the minimum that you need to understand for this course.
We will not be setting up our server to do Reverse DNS Lookups but you are expected to understand the difference, in particular you should understand that:
- Your registrar (whomever you pay for your domain, even if you run your own DNS server) is responsible for normal (forward) DNS resolution of your domain.
- Your ISP (whomever you pay for your internet connection, i.e. the company that assigned a public IP to your server) is responsible for revers DNS lookups for your IP.
INVESTIGATION 1: CONFIGURING DNS SERVER
We will now be installing, configuring and running a DNS server on our vm1.
Preparation
First ensure that the host and domain name is set correctly on each of your four machines (host and three VMs):
- host.yoursenecaid.org
- vm1.yoursenecaid.org
- vm2.yoursenecaid.org
- vm3.yoursenecaid.org
Note that these are settings that are local to each mahcine, e.g. you will still not be able to contact vm1.yoursenecaid.org from vm3. That's because currently you're using the Seneca and other public DNS servers which know nothing about yoursenecaid.org
This preparation step is in fact unnecessary to complete our goal for the lab (do you know why?) but it will make things look more consistent, which will make your life a little easier.
Installation
Use yum to install the DNS server. We'll be using Bind, the most popular DNS server on the planet.
Configuration
An authoritative Bind server has a global configuration file (named.conf) and at least one zone file for the zone it's authoritative for.
/etc/named.conf
When you install Bind you'll get a default '/etc/named.conf'. Move this file over to a backup location, we will be writing one from scratch with the following contents, but use your own X value where applicable.
options {
directory "/var/named/";
allow-query {127.0.0.1; 192.168.X.0/24;};
forwarders { 142.204.1.2; };
};
zone "localhost" {
type master;
file "named.localhost";
};
zone "'''seneca-id'''.org" {
type master;
file "mydb-for-yoursenecaid-org";
};
You need to understand all the options in this file except the localhost zone, so that in the future (for example in a practical test) you can quickly set up a DNS server for a new zone. So look up in the reference these things and write down what they do:
- directory
- allow-query
- forwarders
- type
- file
Zone file
Now edit /var/named/mydb-for-yoursenecaid-org and enter the following (use your own X value where applicable).
$TTL 3D
@ IN SOA vm1.seneca-id.org. webmaster.seneca-id.org.(
1 ; Serial
8H ; Refresh
2H ; Retry
1W ; Expire
1D ; Negative Cache TTL
);
@ IN NS vm1.seneca-id.org.
vm1 IN A 192.168.X.2
Again, here's the reference documentation for records in this file. Pay specific attention to:
- asd
Now that your DNS server (bind, a.k.a. named) is configured:
- Start it with the systemctl command.
- Check that it's running using:
- The ps ax command (perhaps combined with grep)
- A systemctl command
- The system log file /var/log/messages
- Once you're sure the service starts and runs without errors - set it to start automatically when this virtual machine boots.
Firewall rules update
Remember you're supposed to have a working firewall on your vm1 (and every other machine, but this is the one we're concerned with now). A working firewall will block requests to ports that you didn't explicitly allow. Which means at this point your DNS server, even though it's perfetly configured, is inaccessible because iptables won't allow the requests to come in.
You'll need to update the firewall on vm1 to allow incoming connections in UDP port 53 - that's the protocol and port DNS works over. Then save your rules using whatever means worked for you in the iptables labs.
You can just disable the firewall but that is a poor workaround. You're expected to be able to handle configuration like this in this course.
INVESTIGATION 2: CONFIGURING DNS CLIENT
Now that we have setup a DNS server on your virtual machine (vm1), we will now switch to the host machine, and define the name server that is running on vm1 in order to resolve the seneca-id domain name to the appropriate IP address.
Perform the following steps on your Centos host:
- Edit the /etc/resolv.conf file and enter the following:
nameserver 192.168.X.2 domain '''seneca-id'''.org
- Now try the commands:
host host.'''seneca-id'''.org host vm1.'''seneca-id'''.org host vm2.'''seneca-id'''.org host vm3.'''seneca-id'''.org host yahoo.ca
host 192.168.X.1 host 192.168.X.2 host 192.168.X.3 host 192.168.X.4
- Now configure your other virtual machines to also use VM 1 as their DNS server.
- Also on the VMs use a text browser such as lynx to access the Web.
(NOTE: you do not need to authenticate yourself through SeneNet on this machine, as they connects through the host which is already authenticated) - On all machines in your network, experiment with the following commands. Be sure to use several different command options to learn and understand how they work:
host dig nslookup
- Finally, ensure each machine is using the static IP address and hostname that matches what the DNS server now claims they use. Double check that this address, and the ability to search using your DNS server, persist after reboot.
- On each machine add the entry to your interface configuration file that will cause it to permanently use your VM 1 as its primary DNS server.
- If you have made any changes to the /etc/hosts file, undo them. Your machines must be relying on your DNS server.
- Ensure that your machines can ping and SSH to each other by IP address and by name (hostname only, and hostname with domain).
- Modify the ifcfg file on your host so that it will still get a DHCP address, but ignore the DNS information given to it by the DHCP server in favour of the domain and DNS information you provide it.
Record troubleshooting checklist for INVESTIGATION 2 in your OPS335 lab log-book
COMPLETING THE LAB
Upon completion of this lab you have a DNS server in your network and every machine is using it to resolve internal and external hostnames and ip addresses.
You have now gained experience with some common configuration settings for named, as well as common resource records.
Note: Due to the changes made in this lab, you will now need your VM 1 running in order for you host to be able to contact any other machines.
Arrange evidence (command output) for each of these items on your screen, then ask your instructor to review them and sign off on the lab's completion:
- ✓x.
EXPLORATION QUESTIONS
- What iptables rules apply to DNS?
- Under what circumstances does DNS use TCP vs UDP?
- What is a zone file and what is it used for?
- Name the zone files used in this lab, and their purpose.
- What file did you edit to set a static IP address?
- What parameter did you set in that file to tell the machine to refer to your own DNS server?
- What is the purpose of /etc/resolv.conf?
- What is meant by the term "negative cache"?
- What are MX records used for?
- What security features are available for DNS?